Semi-quantum private comparison protocol of size relation with d-dimensional GHZ states
Bing Wang(王冰) San-Qiu Liu(劉三秋) and Li-Hua Gong(龔黎華)
1Jiangxi Province Key Laboratory of Fusion and Information Control,Department of Physics,Nanchang University,Nanchang 330031,China
2School of Materials Science and Engineering,Nanchang University,Nanchang 330031,China
3NCU-ASIPP Magnetic Confinement Fusion Joint Lab,Institute of Fusion Energy and Plasma Application,Nanchang University,Nanchang 330031,China
4Department of Electronic Information Engineering,Nanchang University,Nanchang 330031,China
Keywords: semi-quantum private comparison,size relation,dimensional GHZ state,qubit efficiency
1. Introduction
To date, quantum cryptography has been gained considerable attention worldwide. Many secure quantum cryptographic protocols have been designed, such as quantum key distribution (QKD),[1-5]quantum secret sharing (QSS),[6-8]quantum secure direct communication(QSDC),[2,9-11]and so on. Recently,some new research fields of quantum cryptography have emerged including quantum homomorphic encryption (QHE),[12]quantum information splitting,[13]quantum private comparison (QPC). Since the first QPC protocol was proposed by Yang and Wen in 2009, QPC has become a hot topic.[14]By utilizing Bell state,hash function and decoy photons, their protocol can compare the equality of two parties’secrets. In 2010, Chenet al.devised a new QPC protocols which can also compare the equality of privacies.[15]Later, a new type of QPC protocol allowing clients to execute quantum processing on a remote server was presented,[16]with the duality quantum formalism.[17]Although many QPC protocols were proposed,all participants need to be equipped with advanced quantum devices, such as quantum measurement,quantum state generator, or quantum unitary operation.[18-22]To reduce the consumption of quantum devices,an innovative concept of semi-quantum theory has been put forward.[23,24]In the semi-quantum mode,quantum party owns the powerful quantum capability and can prepare quantum state, perform quantum measurement and store qubits in quantum memory,while classical parties only have limited quantum capability and can perform the following classical operations:
(1)Let particle go back without disturbance.
(2)Measure the particle withZbasis,prepare a new state inZbasis and distribute it back.
(3)Reorder particles with different delay lines.
Not all participants could afford the expensive quantum equipment, semi-quantum theory is very practical and convenient in the near future application, therefore semiquantum key distribution (SQKD),[25-29]semi-quantum secret sharing (SQSS),[30,31]semi-quantum private comparison(SQPC)[32-35]were investigated widely. Chouet al.proposed the first SQPC protocol, allowing two classical participants to compare the equality of their secrets with the help of an almost-dishonest third party.[32]In 2020,Jiang devised two semi-quantum private comparison protocols based on Bell states to compare the equality of two classical participants’ secrets.[36]Most previous private comparison protocols based on semi-quantum theory can only compare the equality of privacies between two classical participants. Fortunately, in 2021, Zhouet al.presented a semi-quantum private comparison protocol to compare the size relationship of two-participant’s secrets under the assistance of a semi-honest third party,and the qubit efficiency is raised to be comparable with the existing semi-quantum private comparison protocols at the cost of preparation of the classical authenticated channel in advance by classical participants.[37]
It is generally known that a quantum two-party secure computation is impossible.[38]However, this goal may be achieved if additional assumptions were made,such as adding a third party. A semi-honest third party (STP) should follow the procedure of the protocol,take a record of all intermediate computation and prevent the results from being corrupted by an outside eavesdropper. However, STP may attempt to steal the information from the record.
Motivated by Refs. [36,37,39], we propose a novel efficient private comparison protocol based on thed-dimensional GHZ states. Under the assistance of a semi-honest third party,our protocol can judge the size relationship of the privacies between Alice and Bob. The rest of this paper is organized as follows: In Section 2,we give a detailed description of the proposed protocol. In Section 3, the correctness of the output result is analyzed and some examples are listed for better understanding. In Section 4, the security of the proposed protocol is analyzed. The attacks from external and internal are invalid to our protocol. In Section 5,the comparisons between our SQPC and those previous typical SQPC protocols are given. Finally,a short conclusion is provided in Section 6.
2. Semi-quantum private comparison protocol of size relation
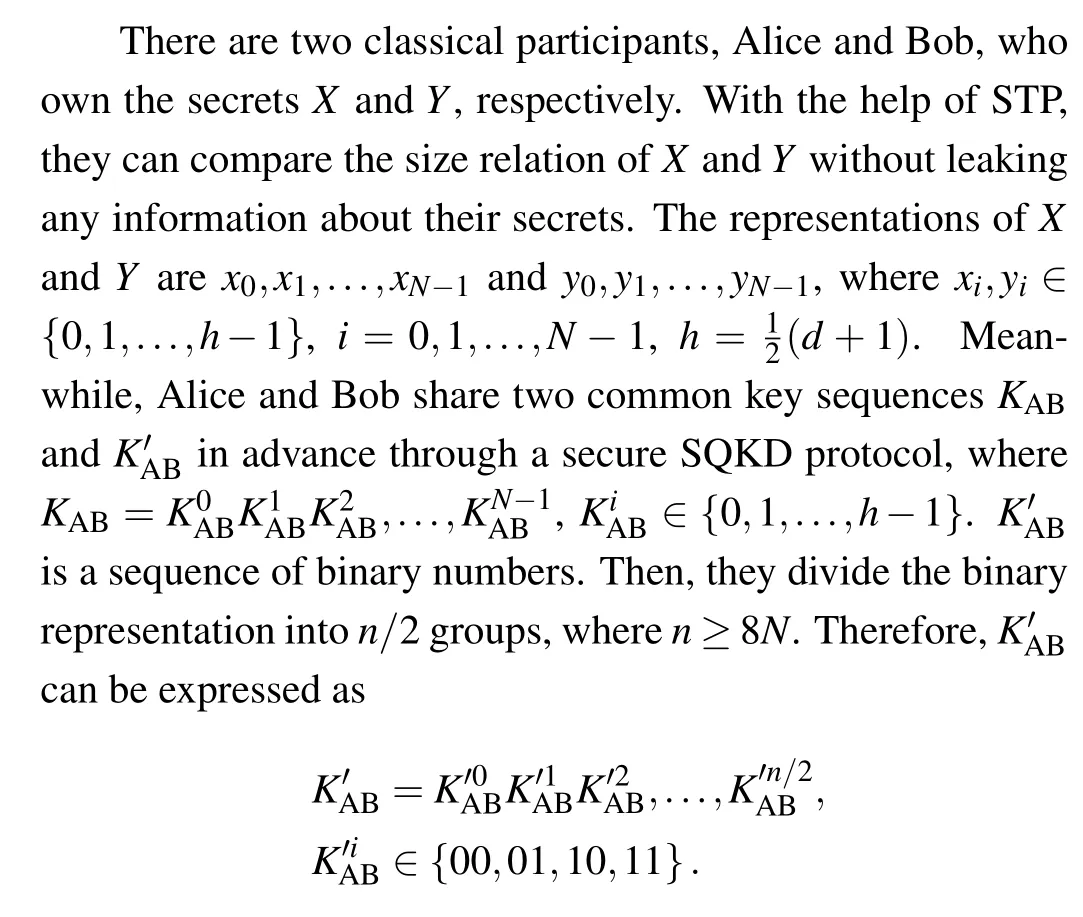
2.1. Preparation for the protocol
The quantum resource used in our SQCP isd-dimensional GHZ state. In ad-dimensional Hilbert space, according to three variablesu1,u2,u3∈{0,1,...,d-1}, ad-dimensional GHZ state can be expressed as[39,40]

Step 3 STP informs Alice and Bob of his receipts and stores sequencesSA′ andSB′ in quantum memory. After that,Alice and Bob announce the operations performed on particles to STP. Based on the announced information, STP selects to execute the corresponding operations demonstrated in Table 2 on these received particles.
Case 1 If both Alice and Bob choose to execute operation(1)on the received particles at the same location(K′iABis 00),then STP will performd-dimensional Bell state measurement on the received particles A and B (action 1). It is well known that three-particle GHZ state can be expressed as
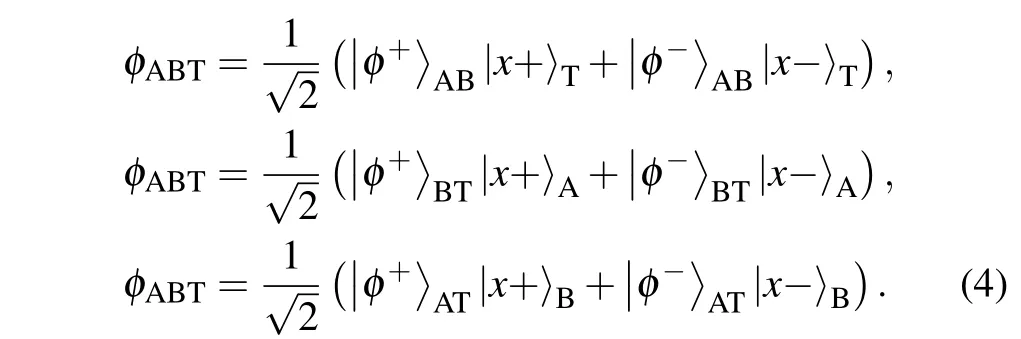
From Eq.(4),STP could know whether there is an eavesdropper or not by comparing the measurement outcomes with the initial states. If the Bell measurement is|φ+〉AB,then there is no eavesdropping,this protocol will proceed to the next case.Otherwise,they will abort the protocol.
Case 2 If Alice chooses to apply operation (1) and Bob executes operation(2)on the received particles at the same location (K′iABis 01), then STP will implement action 2 (STP executesd-dimensional Bell state measurement on particles A and T). From Eq. (4), STP could know whether there is an eavesdropper or not by comparing the measurement outcomes with the initial states. If the Bell measurement is|φ+〉AT,then there is no eavesdropping, this protocol will proceed to the next case. Otherwise,they will abort the protocol.
Case 3 If Alice chooses to apply operation(2)and Bob executes operation (1) (K′iABis 10) on the received particles at the same location, then STP will implement action 3(STP performsd-dimensional Bell state measurement on particles B and T).From Eq.(4)STP could know whether there exists an eavesdropper or not by comparing the measurement outcomes with the initial states. If the Bell measurement is|φ+〉BT,then there is no eavesdropping, this protocol will proceed to the next case. Otherwise,they will abort the protocol.
Case 4 If both Alice and Bob choose to apply operation(2) on the received particles at the same location, then STP will implement action 4 (STP calculatesTi=SiA′?SiB′⊕u2,where?represents the moduledsubtraction). STP can obtain the calculated results sign[Ti],

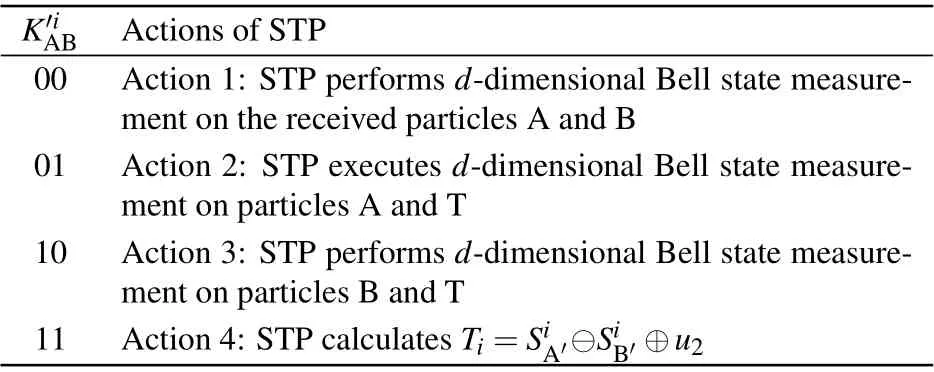
Table 2. Actions of STP.
3. Correctness analyses
3.1. Output correctness
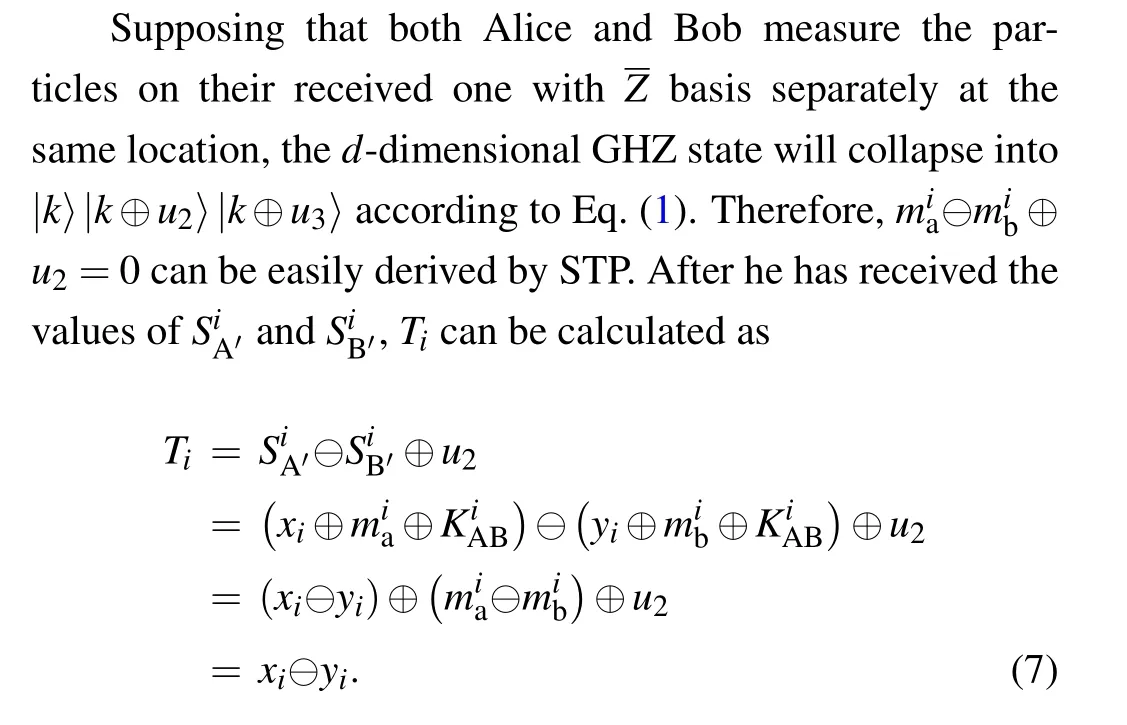
From Eqs. (5) and (6), one can see that if the value ofTiis greater than 0 and less thanh, then STP could obtain sign[Ti]=1,soxi>yi,otherwisexi ≤yi.
3.2. Examples
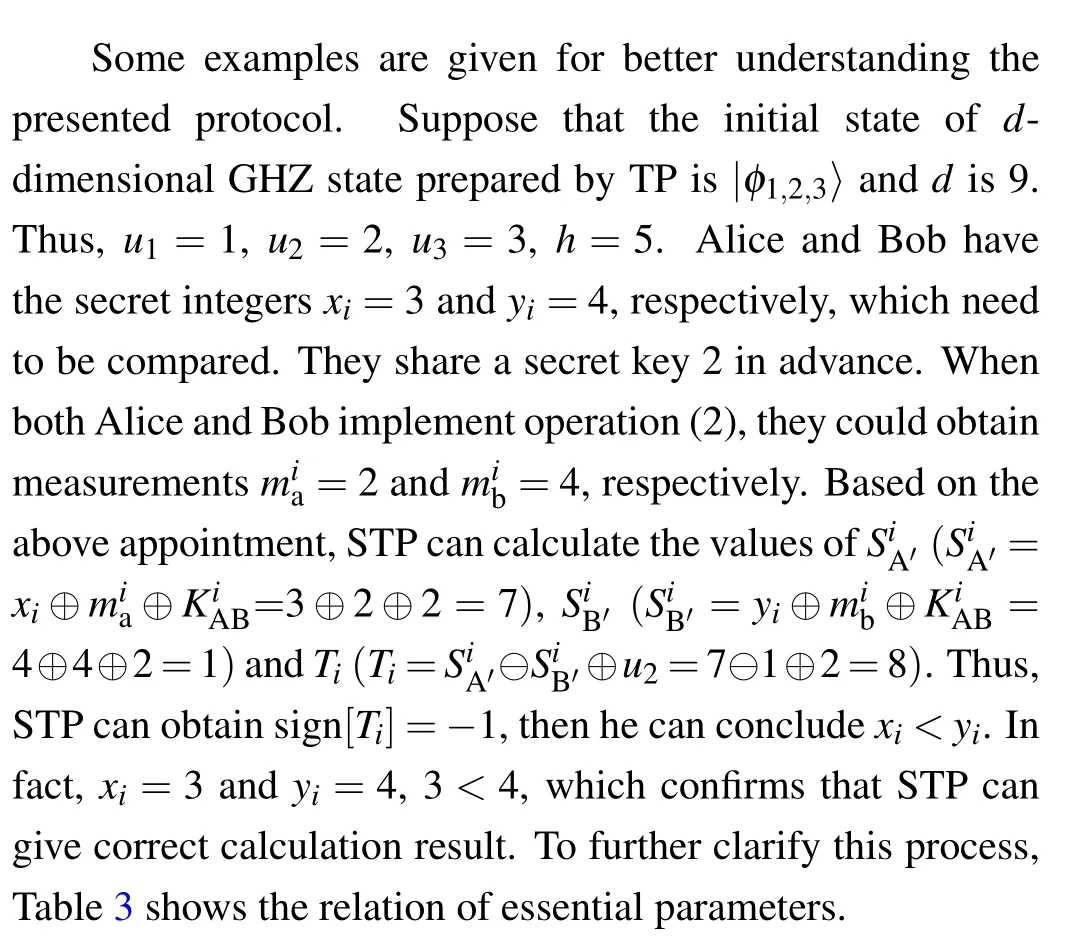
From the examples listed in Table 3,one can see that two participants can achieve a private comparison by the proposed protocol. Meanwhile,it is evident that the correctness and the effectiveness are satisfied.

Table 3. Relation of essential indexes for some examples.
4. Security analysis
4.1. External attack
Eve, an external attack, wants to steal the information from the participants including STP,Alice and Bob. It is well known that as long as there are particles transmitting in the channel, Eve may use many common attacks to obtain some useful information, such as the intercept-measure-resend attack, the entanglement attack and the Trojan horse attack.Next,the security of the proposed protocol will be analyzed.
4.1.1. Intercept-measure-resend attack
In step 1, there are transmissions of particles. Suppose that Eve implements the intercept-measure-resend attack,she would intercept the particles transmitted from STP to Alice(Bob) and measure them with single measurement. Subsequently, she produces new particles whose states are same as the measurement results and sends them to Alice (Bob). Although Eve could not be perceived in cases 4 and 3 (2), her measurement will destroy the correlation of states in cases 1 and 2 (3). From Eq. (4) and Table 2, one can obtain the following details:
In case 1,Eves’measurement will destroy the correlation ofd-dimensional Bell state on particles A and B.
In case 2 (3), Eves’ measurement on particle A (B) will destroy the correlation ofd-dimensional Bell state on particles A(B)and T.
If Eve implements the intercept-measure-resend attack to each particle from sequenceSA(SB), the probability that she was not found is 1/2. Thus, the total probabilitypthat he would not be detected is 1/24N, where 4Nis the total number of GHZ states prepared by STP. Via preparing plenty ofd-dimensional GHZ states, the probability that STP detects Eve’s operation is approximately 1. It can be concluded that Eve cannot obtain any information about the secretsXandYfrom Alice and Bob by launching the intercept-measureresend attack without being discovered in step 1.
In step 2, Alice (Bob) sends sequenceSA′(SB′) to STP.Although there are transmissions of particles, Eve does not know the choice of Alice(Bob)in advance and cannot do exactly as what Alice (Bob) does. Provided that Eve conducts measurement on these particles in cases 1,2 and 3,it will cause errors and destroy the correlation of these Bell states. In case 4,though Eve may get the values ofSiA′andSiB′,she does not knowmiaandmib. Therefore,it can be concluded that Eve cannot obtain any information about secretsXandYfrom Alice and Bob by launching the intercept-measure-resend attack in step 2.
In step 3, because there is no particle transmission, the secrets ofXandYwill not leak.
4.1.2. Entangle attack
When the particles were transmitted in the quantum channel,Eve may use entanglement attack to obtain more information. First,Eve will apply unitary operationUE,and then she will attach an auxiliary entanglement state|E〉to these particles as follows:[39]

Equation(13)tells us that Eve does not discriminate|ε00|from others. That is to say,Eve cannot obtain any information from the particles transmitted in quantum channel by launching entanglement attack on our protocol.
4.1.3. Trojan horse attack
Since the particles prepared by STP in the beginning are transmitted in a round trip in our protocol, Trojan horse attack should be considered as an outside eavesdropper, which generally includes invisible photon eavesdropping attack and delay-photon attack.[42,43]To resist these kinds of attacks,every participant should be equipped with photon filter and photon number splitter. For example,the particle receiver inserts a photon filter in the front of her(his)devices to filter out the photon signal with an illegitimate wavelength,which can withstand the invisible photon eavesdropping and the Trojan horse attack.
4.2. Internal attack
Participant attack,an attack from dishonest participant,is more powerful.[44]We will analyze the attacks from two types of participants,i.e.,dishonest Alice(Bob)and semi-dishonest TP.
4.2.1. Attack from dishonest Alice (Bob)
Without loss of generality, the role of Alice is similar to Bob’s. One only analyzes the chance of Alice stealing Bob’s key. Alice(Bob)attempts to obtain some informationSB(SA)from step 1 andSB′(SA′)from step 2.
In steps 1 and 2,although Alice and Bob shared the same key, they do not know the corresponding rules between the keys and the specific operation of the other participant. Therefore, Alice’s (Bob’s) attack will be detected as an external attack as described in Section 4.11. Hence, one can draw a conclusion that Alice(Bob)could not have the knowledge of secretX(Y).
4.2.2. Attack from semi-dishonest TP
We know that STP can obtain the information fromSA(SB)andSA′(SB′)easily,which provides him more power to attack the protocol. However, sinceKABis distributed between Alice and Bob via a secure QKD protocol, STP is unable to learn the value ofKAB. That is,STP cannot learn any information from the secretsXandYby launching the internal attack.
5. Discussion
The comparisons among our protocol and those previous typical SQPC protocols in Refs. [35-37] are compiled in Table 4.
Like the protocol in Ref. [37], our protocol could also compare the size relation of two classical participants’ input integers,while the SQPC protocol in Refs.[35,36]only could compare the equality of them.
It is well known that the qubit efficiency is expressed ase=bc/bt, wherebcis the number of compared bits in each comparison andbtis the total number of generated particles in each comparison. Applying our protocol to compare twoparty secrets of 2 bits,TP should produce fourd-dimensional GHZ states, i.e., twelve particles. Alice (Bob) selects operation (1) or (2) with equal probability, twoZbasis particles are generated by her(him). Therefore,the qubit efficiency of our protocol is 12.5%. Although most of the protocols mentioned in Table 4 need to share the key in advance, the qubit efficiency of our protocol is the highest,while that in Ref.[35]is the lowest.
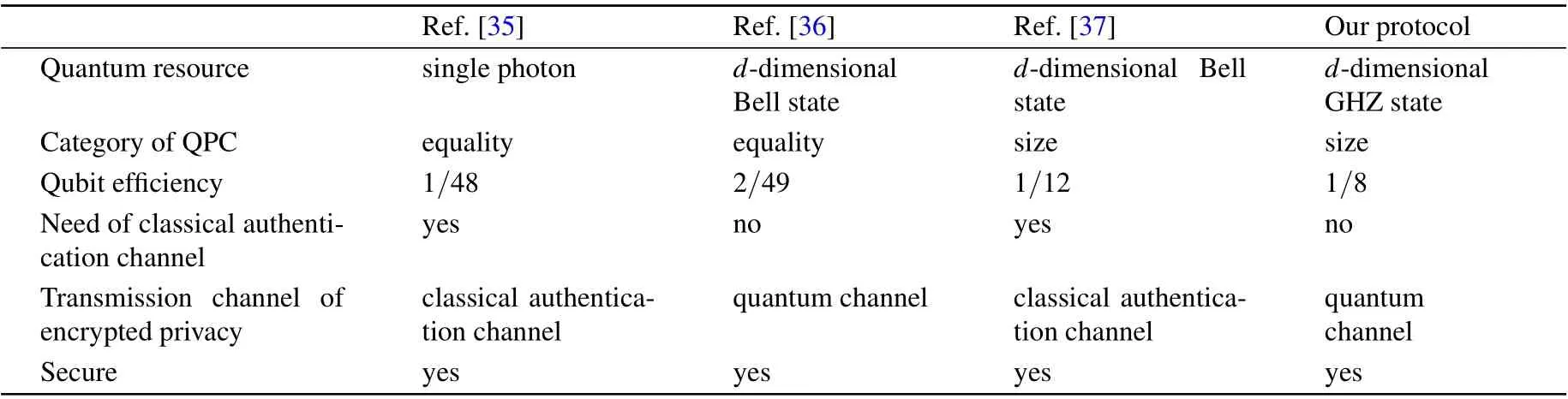
Table 4. Comparisons between our SQPC and those previous SQPC protocols.
The classical participants do not need to prepare classical authentication channel in our protocol in advance, which makes the private comparison easier to operate. In addition, the encrypted privaciesSiA′=xi ⊕mia⊕KiABandSiB′=yi ⊕mib⊕KiABare sent to STP via quantum channel, which reduces the probability of information leakage.
In our protocol, all participants hardly disclose any information about particles including the position and values of some particles, which can also greatly reduce the possibility of information leakage.
6. Conclusion
Based on the entangledd-dimensional GHZ states,a new efficient semi-quantum private comparison protocol is presented with the help of a semi-honest TP. Our protocol can compare the size relation of private information between two classical participants. Compared to existing SQPC protocols,our protocol could achieve higher qubit efficiency.
Acknowledgements
Project supported by the National Natural Science Foundation of China (Grant Nos. 62161025 and 61871205), the Project of Scientific and Technological Innovation Base of Jiangxi Province, China (Grant No. 20203CCD46008), and the Jiangxi Provincial Key Laboratory of Fusion and Information Control,China(Grant No.20171BCD40005).
- Chinese Physics B的其它文章
- Role of compositional changes on thermal,magnetic,and mechanical properties of Fe–P–C-based amorphous alloys
- Substrate tuned reconstructed polymerization of naphthalocyanine on Ag(110)
- Anti-PT-symmetric Kerr gyroscope
- Information flow between stock markets:A Koopman decomposition approach
- Cascading failures of overload behaviors using a new coupled network model between edges
- High efficiency ETM-free perovskite cell composed of CuSCN and increasing gradient CH3NH3PbI3

