ID-Based User Authentication Scheme for Cloud Computing
Ping-Liang Chen, Jen-Ho Yang, and Ching-I Lin
1. Introduction
Nowadays, cloud computing[1]has become a very important issue for information science and the computer industry. Thus, an increasing number of cloud techniques are being developed to make cloud computing more efficient and convenient. Cloud computing can be simply explained as the techniques which manage services (such as information, tools, applications, or programs) for users in remote servers on the Internet. Then, the users can easily access these services via the Internet without keeping a large amount of information on their desktops or mobile devices. Because the services have to be transmitted via the Internet, network security has become a major problem for cloud computing.
In cloud computing applications, user authentication is an important security mechanism because it provides the authentication, authorization, and accounting (AAA) for cloud users and servers. Most cloud computing applications have adopted OpenID[2]-[4]as the user authentication method. The OpenID technique allows the user to utilize one single identity (ID) to access different services among different servers. Thus, the user does not need to maintain several identities for different cloud servers. However,OpenID needs an ID provider to generate a unique ID for every user, so the server has to connect to the ID provider via the Internet while authenticating the user each time.This increases the authentication time and communication load. To solve the above problem of OpenID, we have used the ID-based[5]technique to design an efficient user authentication scheme for cloud computing.
The ID-based scheme formulates the user’s ID as a public key so that it can be directly used to authenticate the user. In recent years, various ID-based authentication schemes[6]-[11]have been proposed to solve user authentication problems on the Internet. In 2004, Das et al.[7]proposed a remote user authentication scheme using a smart card. Their scheme allows users to choose and change their passwords freely without any verifier table. In 2009, Wang et al.[9]pointed out that Das et al.’s scheme could not resist impersonation attacks from a remote server.Thus, Wang et al. proposed an enhanced remote authentication scheme to deal with the security problem.After that, Lee et al.[11]found that Wang et al.’s scheme could not withstand message alteration or impersonation attacks. However, Lee et al. did not propose any improvement scheme to overcome the security flaws of Wang et al.’s scheme.
Because the user’s ID can be directly used for user authentication, the ID-based concept is very suitable for our purpose to design a new user authentication scheme for cloud computing. In this paper, we propose a new ID-based user authentication scheme for cloud computing. The proposed scheme allows the user to log in to different cloud servers using one single ID. Thus, it is not necessary to maintain different IDs for different cloud servers. In addition, the proposed scheme has less computation and communication costs, so it is very suitable for the cloud user who uses a mobile device to access cloud services.
2. Review of ID-Based Authentication Scheme
Wang et aal.’s ID-basedauthenticatioon scheme caan be diivided into twwo phases: tthe registratioon phase andd the auuthenticationphase. Table1 shows thenotations used in thheir scheme. AAnd the two phhases are described as follows.
The steps oof registrationphase shownin Fig. 1 are:
Step 1. Uicchooses IDiannd PWi, and thhen he/she sennds it too S for registraation.
Step 2. S cchooses a secrret value γ annd a one-wayhash fuunction h(?). TThen, S compputes Ni=h(PWWi)⊕h(x)⊕IDiand sttores {h(?), Ni,, γ} into a smaart card.
Step 3. The server sendds PWiand thee smart card tto Uiviia a secure channel.
The steps oof authentication phase as shhown in Fig. 22:
Step 1. UUiuses the ssmart card too compute CCIDi=h((PWi)⊕h(Ni⊕γ⊕TS)⊕IDiaand sends {IDDi, CIDi, Ni, TSS} to S.
Step 2. S cchecks if TS iis a valid timee. If TS is invvalid,thhen S rejects thhis login requuest.
Step 3. Scomputes h′(PWi)=CIDi⊕h(Ni⊕γ⊕TS)⊕IDiannd ID′= Ni⊕h(x)⊕h′(PWi)). Then, S chhecks if ID′==ID
iiihoolds. If the equation holdss, then Uiisauthenticatedas a leegal user.
Step 4. S coomputes a′=h(h′(PWi)⊕γ⊕TS*) and sendds (a′,TTS*) to Ui.
Step 5. Uichecks if TS**is a valid timme. If TS*is vvalid,thhen Uicompuutes a=h(h(PWWi)⊕γ⊕TS*)and checks if the eqquation a=a′ hholds. If a=a′, then Uicanbe sure that SS is a vaalid server.
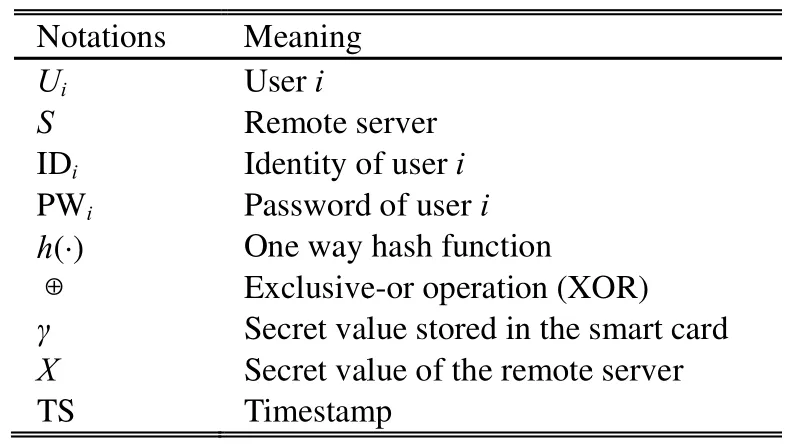
Tablee 1: Notations of Wang et al.’s scheme
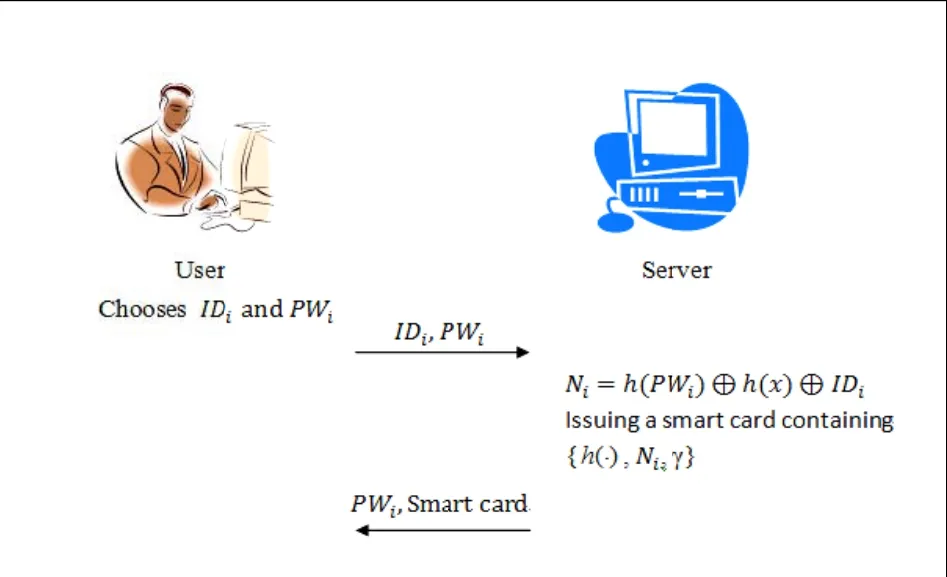
Fi g. 1. Registrati on phase of Wa ng et al.’s sche me.
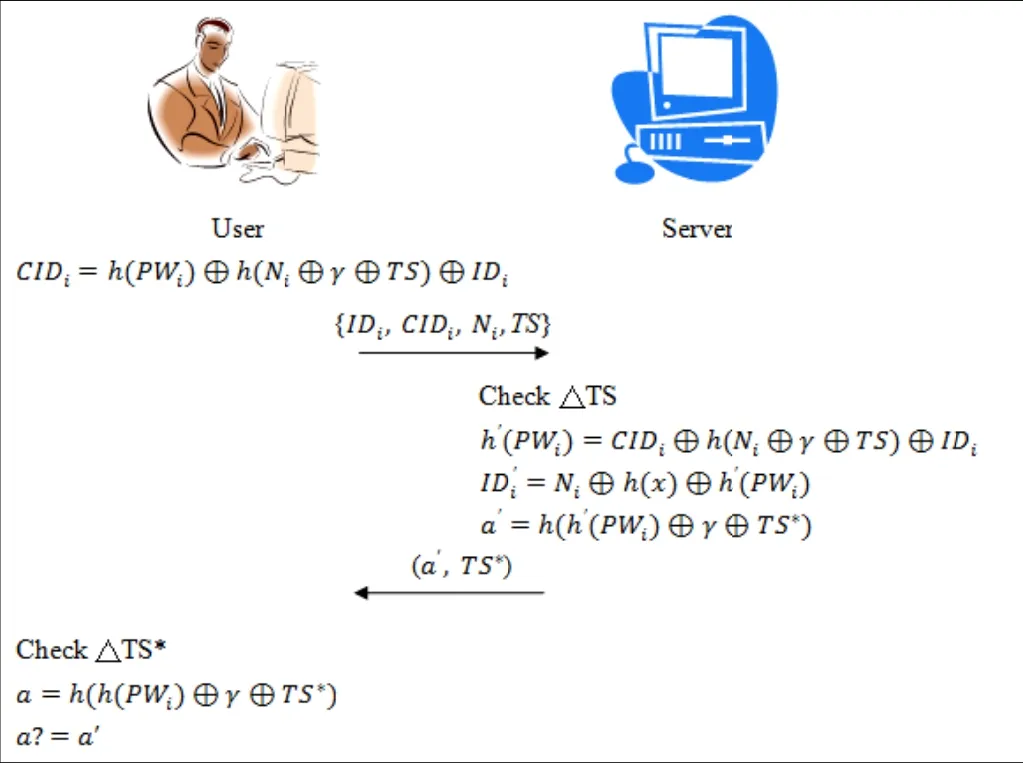
Fig.2. Authenticati on phase of Waa ng et al.’s schee me.
Lee et al.[11]pointed outthat Wang eet al.’s schemme could not withstand themessagealterationor impersonation atttacks. But, Leee et al. did nnot propose anny imprrovement metthod in their aarticle. Besidess, we found thhat Wanng et al.’s schheme has largge computatioon costs on the userr side and soo it is not suuitable for clloud computing appllications. Theerefore, we prropose a neww ID-based user authhentication sccheme for clooud computinng in the next sectiion.
3.Propose d Scheme
The proposedd ID-based usser authentication schemeis divided into twoo phases: thee registrationphase and the mutuual authentication phase.The notations used in our scheeme are shownn in Table 2.
The registratioon phase:
In this phasee, the clouduser gets the authenticatioon information fromm an IDprovider. Note that tthe authhentication innformation iss transmittedvia a secuure channnel. The steps of this phasee are shown as Fig. 3.
Step 1. Thecloud user seends IDuand IDsto the IID provvider for registration.
Step 2. The IDD provider uses its secret key x to compuute Pu=hh(IDu⊕x) andd Su=h(Pu). Then, the ID provider sendsPuto thhe user via a secure channel.
Step 3. The IID provider sends IDuandSuto the clouud servver.
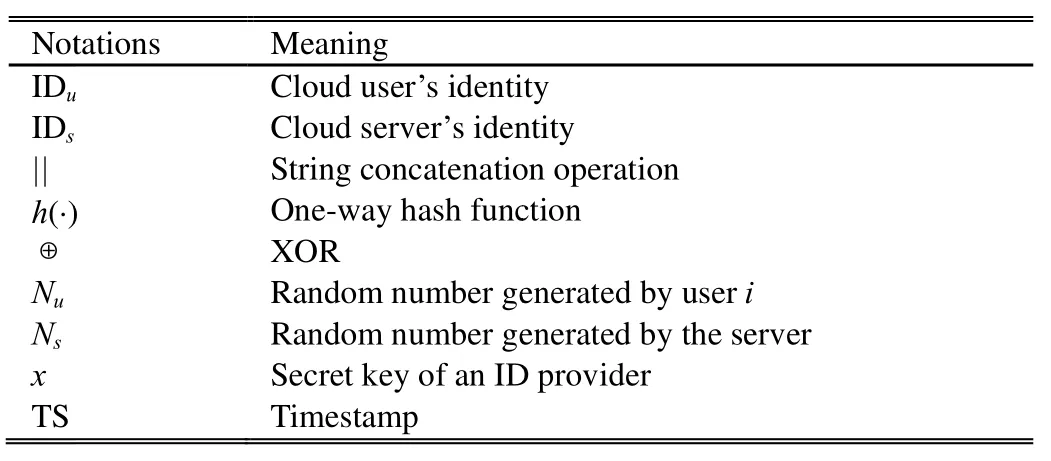
Table 2: Notations useed in the propose d scheme
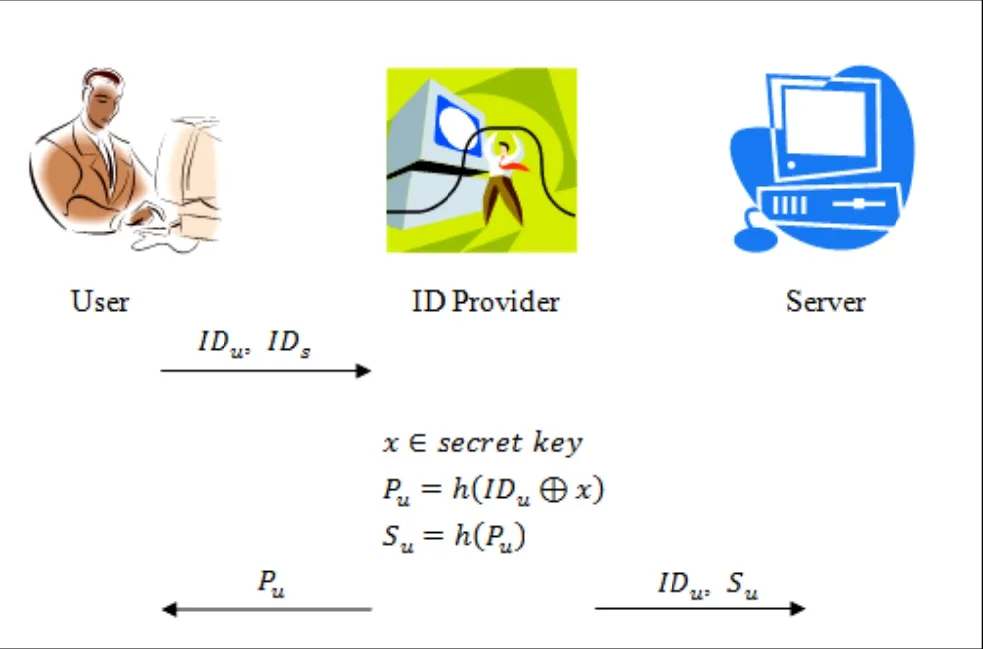
Fii g. 3. Registratii on phase of thee proposed scheem e.
Mutual autthentication phhase:
In this phaase, the user llogs in to thee server usingg IDuannd Pu. Then,the server caan authenticatte the user by IDuannd Pu. In addiition, the usercan also authhenticate the server too accomplishthe mutual auuthentication.The steps of this phhase are showwn as follows.
Step 1. Thhe user generaates a randomm integer Nuand a timestamp TSto computeCIDu=h( h( PPu) IDuTS)⊕Nuannd Au=h(Nu).Then, the useer sends (CIDDu, Au, IDu, TS) to thhe server.
Step 2. Thee server checkks if TS is vaalid. If TS is vvalid,thhen the serverr computes= C IDu⊕hh( SuIDsTS)and AAu′= h (). Iff Au′ =Auhoolds, then theserver can bee sure thhat the user islegal.
Step 3. Thee server generrates a randomm integer Nsand a timestamp TS*to compute CID =h( SSID TS*)⊕Nsu s s and Bs=h(Ns). TThen, the servver sends (CIDDs, Bs, IDs, TSS*) to thhe user.
Step 4. Thee user checkss if TS*is valiid. If TS*is vvalid,thhen the usercomputes NN′= C ID⊕hh( h( P)ID TTS*)
s s u s annd Bs′=h( Nss′ ). If Bs′=Bsholds, thenn the user caan be suure that the seerver is legal.
Accordingto the abovee steps, the prroposed schemme is deesigned by onne-way hashfunctions andd XOR operattions,annd thus has loow computatioon costs for clooud users. Besides,thhe user’s autheentication infoormation is generated by the ID prrovider. Thereefore, the prooposed schemee is easily applied too multi-serverr environmentts. That is, thee user can use one IDD to log in todifferent clouud servers.
4. Security Analyses and Discussio ns
In this secttion, we show that the proposed scheme can prevent somepossible attacks, such as outsider attacks,insider attacks, impersonation attacks, and replay attacks.The security annalyses are described as follows.
Outsider Attack:
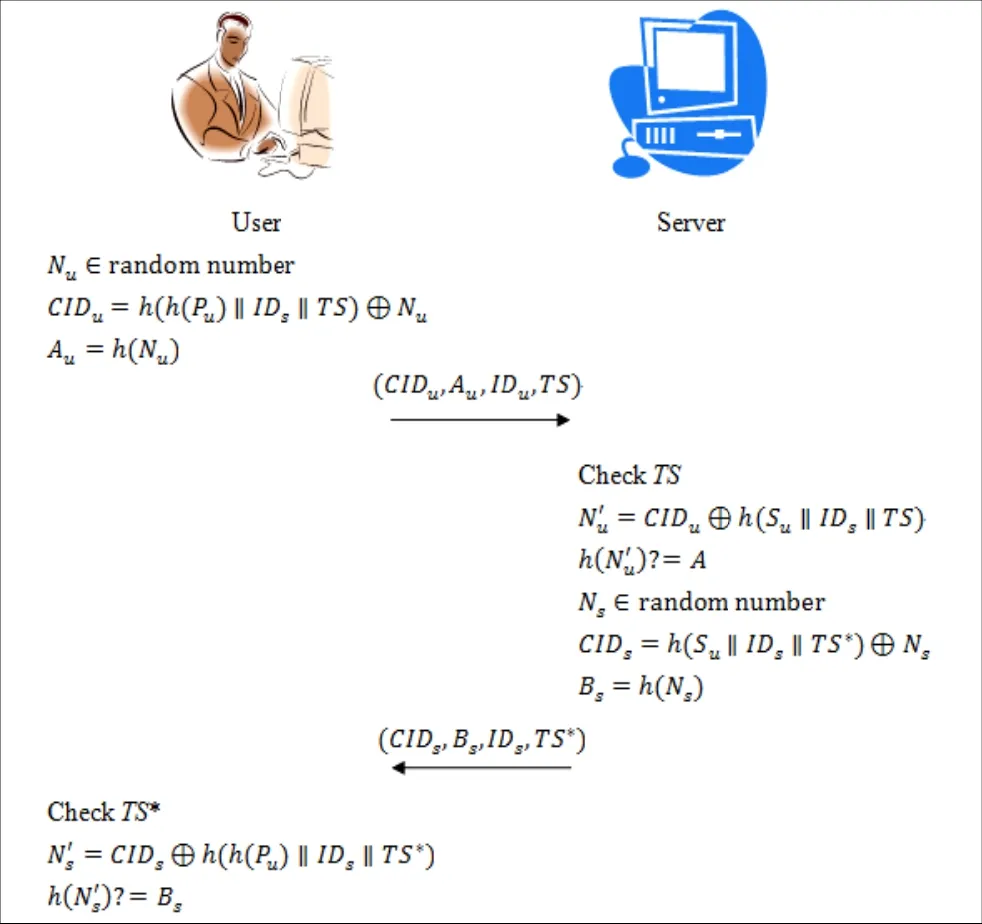
Fig.4. Mutual authee ntication phas e of the proposed scheme.
Assume thaat an attackker wants tto obtain the authentication infformation Pu==h(IDu⊕x), andd so eavesdrops onthe communications toget CIDu=h( h( Pu)IDsTS)⊕Nu. Then,the attackermay try to coompute Pufroom CIDDu. However,this attack iis impossiblebecause Puis prottected by theone-way hashh function h(?) and a randoom nummber Nu. Onn the otherhand, compuuting Pufroom CIDD =h( S IDTS*)⊕N iis also imposssible becausePu
su ssis pprotected bythe one-wayy hash functiion h(?) anda randdom number NNs.
IInsider Attackk:
AAssume that aa legal user wwants to obtainn the secret kkey x off the cloud sserver, and hhe/she may coompute x from Pu=hh(IDu⊕x). However, this atttack is infeasiible because x is prottected by thee one-way haash functionh(?). Similarly,commputing x froom Su=h(Pu)on the serveer side is also infeasible becausee x is protecteed by h(?).
IImpersonationn Attack:
AAssume thatan attacker wwants to impersonate a leggal userr IDuto log inn to the serveer, and he/she may choosee a fakee Pu′ to compute CIDD′u= h ( h( Pu′ )IIDsTS)⊕Nuu.Thenn, the attaccker sendsCID′utothe serverto impersonate IDu.However, thee server willfind that CID′u is sent from anattacker because Su≠h(Pu′). Thus, tthe attaccker cannot iimpersonate aa legal user iin the proposed scheeme. Similarlly, an attackker cannot immpersonate tthe servver because hee/she does notknow the corrrect Su.
RReplay Attackk:
AAssume thatan attacker inntercepts thecommunicatioon betwween the userand a server,and he/she caan get (CIDu, AAu,IDu,TS). Then, tthe attacker reeplaces TS byy TS′ and sennds(CIDu, Au, IDu, TS′) to log in to the server, and the server computesNu′= C IDu⊕ h ( SuIDsTS′) and Au′= h( Nu′).Then, the server knows that Au′ ≠Aubecause TS′≠TS.Therefore, the server will discover that (CIDu, Au, IDu, TS′)is transmitted from an attacker. That is, the proposed scheme can prevent replay attacks.
5. Conclusions
In this paper, we propose an ID-based user authentication scheme for cloud computing. Compared with the related works, the proposed scheme has less computation costs because one-way hash functions and XOR operations are used. In addition, the proposed scheme allows the user to access different servers using one single identity. Thus, it can be efficiently applied to multi-server environments for cloud computing. Based on the proposed scheme, we plan to investigate a new user AAA scheme for cloud computing which can be applied to more applications for cloud computing in the future.
[1] IMC advanced learning solutions. What is cloud computing.[Online]. Available: http://www.im-c.com/en/products/learning-management-system/clix-saas/what-is-cloud-comp uting.
[2] B. Wang, H.-Y. Huang, X.-X. Liu, and J.-M. Xu, “Open identity management framework for SaaS ecosystem,” in Proc. of 2009 IEEE Int. Conf. on e-Business Engineering,Macau, 2009, pp. 512-517.
[3] OpenID. [Online]. Available: http://en.wikipedia.org/wiki/OpenID
[4] GoogleFriend connect. [Online]. Available: http://zh.wikipedia.org/zh-tw/Google%E6%9C%8B%E5%8F%8B%E 7%BE%A4
[5] A. Shamir, “Identity based cryptosystems and signature schemes,” in Proc. of CRYPTO’ 84 on Advances in Cryptology, Santa Barbara, 1984, pp. 47-53.
[6] M.-S. Hwang, J.-W. Lo, and S.-C. Lin, “An efficient user identification scheme based on ID-Based cryptosystem,”Computer Standards and Interfaces, vol. 26, no. 6, pp.565-568, 2004.
[7] M. L. Das, A. Saxena, and V. P. Gulati, “A dynamic ID-based remote user authentication scheme,” IEEE Trans.on Consumer Electronics, vol. 50, no. 2, pp. 629-631, 2004.[8] C.-C. Chang and J.-H. Yang, “An efficient ID-based user identification scheme for mutual authentication in mobile environments,” Journal of Discrete Mathematical Sciences and Cryptography, vol. 9, no. 3, pp. 537-548, 2006.
[9] Y. Wang, J. Liu, F. Xiao, and J. Dan, “A more efficient and secure dynamic ID-based remote user authentication scheme,” Computer Communications, vol. 32, no. 4, pp.583-585, 2009.
[10] J.-H. Yang and C.-C. Chang, “An ID-based remote mutual authentication with key agreement scheme for mobile devices on elliptic curve cryptosystem,” Computers &Security, vol. 28, no. 3-4, pp. 138-143, 2009.
[11] H. Lee, D. Choi, Y. Lee, D. Won, and S. Kim, “Security weaknesses of dynamic ID-based remote user authentication protocol,” World Academy of Science, Engineering and Technology, vol. 59, pp. 190-193, Nov. 2009.
 Journal of Electronic Science and Technology2013年2期
Journal of Electronic Science and Technology2013年2期
- Journal of Electronic Science and Technology的其它文章
- Call for Papers Journal of Electronic Science and Technology Special Section on Terahertz Technology and Application
- JEST COPYRIGHT FORM
- Interpurchase Time of Customer Behavior in Cloud Computing
- A Genetic Algorithm Based Approach for Campus Equipment Management System in Cloud Server
- Toward Cloud-Based Parking Facility Management System: A Preliminary Study
- A Distribution Management System for Relational Databases in Cloud Environments
