Side Information-Based Stealthy False Data Injection Attacks Against Multi-Sensor Remote Estimation
Haibin Guo , Zhong-Hua Pang ,,,and Chao Li
Dear Editor,
This letter investigates a novel stealthy false data injection (FDI)attack scheme based on side information to deteriorate the multi-sensor estimation performance of cyber-physical systems (CPSs).Compared with most existing works depending on the full system knowledge, this attack scheme is only related to attackers’ sensor and physical process model.The design principle of the attack signal is derived to diverge the system estimation performance.Next, it is proven that the proposed attack scheme can successfully bypass the residual-based detector.Finally, all theoretical results are verified by numerical simulation.
CPSs integrate computation, communication and control, breaking through the geographical restrictions in traditional control modes,which have been widely applied to many fields such as power grid,smart factory, and multi-agent systems [1], [2].However, communication networks incidentally increase the operation risk of CPSs, e.g.,external cyber intrusions [3], [4].Thus, the security of CPSs is of great importance and has attracted more attention in recent years.
As one of typical cyber attacks, stealthy FDI attacks hold the greater damage on the system performance meanwhile evading the anomaly detector [5].In [6], a residual-based linear attack scheme was proposed to maximally degrade the performance of remote estimation without causing the alarm of χ2detector.Then, a historical and current residuals-based attack scheme was developed in [7] to further improve the attack impact.And, in [8], an extra sensor was adopted by the attacker to obtain side information that was utilized to design the attack signal.Both side information and historical residual were employed in [9] to construct the attack scheme.In [10], the security protection of multi-sensor remote estimation was investigated, and it was analyzed and proven that such a system can effectively expose the above single-sensor attack schemes.However, few works investigate the stealthy FDI attacks against the multi-sensor remote estimation except [11], [12].The stealthy FDI attack schemes proposed in [11], [12] required the full system knowledge as well as depending on the measurement information of all sensors.Compared with such a case, it is relatively easy and freedom for malicious attackers to measure the output of the target system by their own sensor [8], [9].Furthermore, the remote center is carefully protected in general, and it is very difficult to illegally disclose its knowledge[13].
This letter considers a more reasonable and practical scenario that malicious attackers only know the physical system model and the side information measured by the extra sensor.The specific contributions of this letter are detailed as follows.1) For the multi-sensor remote estimation, a novel stealthy FDI attack scheme, which is only related to the side information, is proposed to maximally damage the system estimation performance meanwhile evading the residualbased detector.2) The design principle of attack signal is derived to cause the estimation error to diverge.And, it is proved that the statistical distribution of the compromised residual is the same as the normal case, which illustrates the stealthiness of the proposed attack scheme.
Notations: Rndenotesn-dimensional Euclidean space.Φ>0(Φ ≥0) denotes Φ is a positive definite (semi-definite) matrix.N(q,Q)denotes the Gaussian distribution with meanqand covarianceQ.E[·] denotes the mathematical expectation.Ipdenotespdimensional identity matrix, and 0 denotes the zero matrix with appropriate dimensions.
Multi-sensor remote estimation: Consider a linear time-invariant discrete-time system withNsensors

Remark 1: As shown in (3) and (10), both the system sensors and the extra sensor are employed to measure the information of the physical system.Compared with utilizing the information of all system sensors and the full system knowledge to design the attack signal in [11], [12], it is more freedom for the proposed attack scheme to merely require the partial physical system knowledgeAand the side information measured by the extra sensor.And, it can be found from(16)–(18) that the injection signal γkis unrelated to the real-time measurement information.Furthermore, the filter gainKain (11)needs to guaranteeA-KaCeAstable, which is unrelated with the Kalman filter (6).These break through the strict assumptions of attack design and reduce the attack complexity.
Attack destructiveness: Under the attack, the entire measurement(3) is rewritten as
Correspondingly, the residual received by the remote center becomes
based on which, the Kalman filter (6) is redescribed as
which is utilized to quantify the estimation performance of the compromised system.
Theorem 1: Under the attack, the estimation errordiverges, if and only if the system matrixAis unstable or the attack signal αkis unbounded.
Proof: Combining with (13), (14), (20) and (21) yields
Then, with (16) and (18), the injection signal (17) satisfies

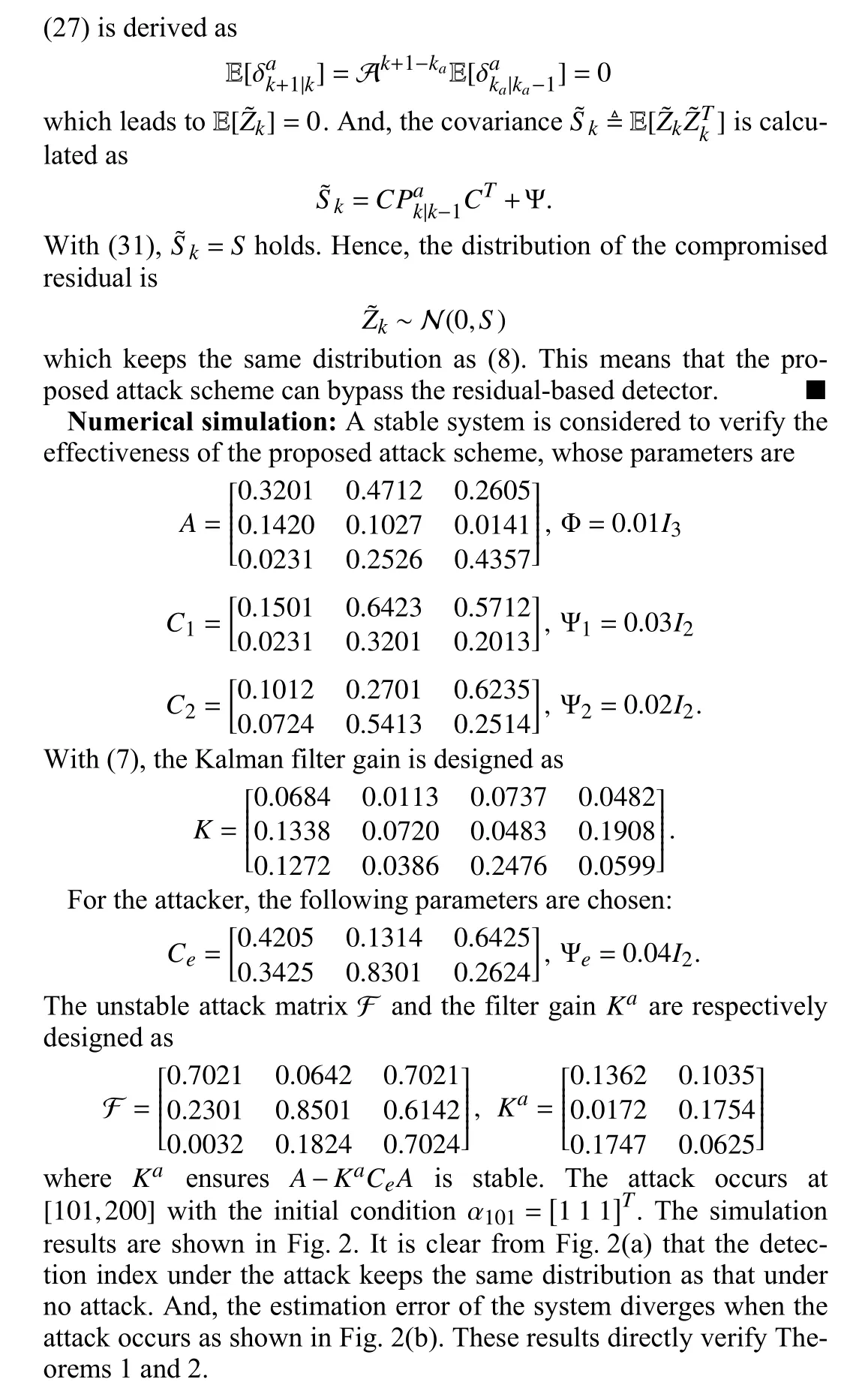
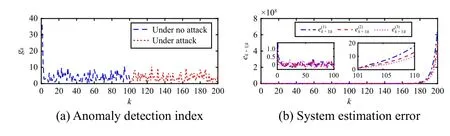
Fig.2.The system performance under attack.
Conclusion: This letter has explored the security issue of multisensor remote estimation of cyber-physical systems from the adverse standpoint.A stealthy FDI attack scheme, which is based on the side information measured by an extra sensor, has been proposed.The design principle of the attack signal has been derived for stable and unstable systems aiming at extremely degrading the estimation performance.Then, the distribution of the polluted residual has been derived to illustrate the attack stealthiness.Finally, the numerical simulation has been carried out to verify the effectiveness of the proposed attack scheme.In our future work, the proposed scheme will be further investigated for the cooperative control of networked multi-agent systems [14].
Acknowledgments:This work was supported in part by the National Natural Science Foundation of China (62173002) and the Beijing Natural Science Foundation (4222045).
 IEEE/CAA Journal of Automatica Sinica2024年4期
IEEE/CAA Journal of Automatica Sinica2024年4期
- IEEE/CAA Journal of Automatica Sinica的其它文章
- Parameter-Free Shifted Laplacian Reconstruction for Multiple Kernel Clustering
- A Novel Trajectory Tracking Control of AGV Based on Udwadia-Kalaba Approach
- Attack-Resilient Distributed Cooperative Control of Virtually Coupled High-Speed Trains via Topology Reconfiguration
- Synchronization of Drive-Response Networks With Delays on Time Scales
- Policy Gradient Adaptive Dynamic Programming for Model-Free Multi-Objective Optimal Control
- Lyapunov Conditions for Finite-Time Input-to-State Stability of Impulsive Switched Systems
