A universal protocol for bidirectional controlled teleportation with network coding
Meng-Yao He, Song-Ya Ma,2,3 and Kun-Peng Kang
1 School of Mathematics and Statistics, Henan University, Kaifeng 475004, China
2 Information Security Center, State Key Laboratory of Networking and Switching Technology, Beijing University of Posts and Telecommunications, Beijing 100876, China
3 Henan Engineering Research Center for Artificial Intelligence Theory and Algorithms,Henan University,Kaifeng 475004, China
Abstract We investigate bidirectional teleportation that works in a fair and efficient manner.Two explicit protocols are proposed to realize bidirectional teleportation with a controller.One is a symmetric protocol for two-qubit states.The other is an asymmetric protocol for single- and two-qubit states.We then devise a universal protocol for arbitrary n1- and n2-qubit states via a(2n1+2n2+1)-qubit entangled state, where n1 ≤n2.The receiver only needs to perform the single-qubit recovery operation, which is derived by a general expression.Moreover, a(2n1+1)-bit classical communication cost can be saved within the controller’s broadcast channel by the use of network coding technology.
Keywords: bidirectional controlled teleportation, network coding, projective measurement,recovery operation
1.Introduction
Quantum entanglement has been exploited as a fundamental resource for the implementation of quantum informationprocessing tasks.For example, Gong et al [1] proposed a quantum network dialogue protocol based on continuousvariable Greenberger-Home-Zeilinger (GHZ) states.Zhou et al [2] proposed a semi-quantum key distribution protocol with four-particle cluster states.Ma et al [3] investigated probabilistic quantum network coding over a butterfly network via non-maximal entanglement.In 1993, Bennett et al[4] first presented a remarkable protocol called quantum teleportation (QT) that securely transmits an unknown qubit state based on the dual use of classical and quantum channels.A different kind of QT scheme, controlled quantum teleportation (CQT) was introduced by Karlsson et al [5] to realize teleportation under the supervision of a controller.Although the controlling party does not own the teleported state, he decides whether the state can be recovered by the receiver.In addition, theoretical generalizations have been proposed, such as probabilistic QT, [6] hierarchical QT,[7] QT in noisy environments, [8, 9] etc.Meanwhile, experimental implementations of QT have also been reported [10, 11].
In addition to one-way QT, for a practical quantum network that contains many processors working far apart, an exchange of information states between two parties may be required.This is possible simply by switching on two sets of independent QT equipment in opposite directions.Since standard QT needs to send a classical message about the measurement result from the sender to the receiver,a situation may arise in which Alice’s state has been teleported to Bob,but Bob decides not to tell Alice about his measurement result.This leads to an insecure or dishonest quantum communication.Therefore, it is necessary to investigate bidirectional quantum teleportation that works in a fair manner.Mishra et al [12] presented a controlled communication scheme which can simultaneously exchange two unknown single-qubit states via a six-qubit entangled channel.Nevertheless, Alice and Bob cannot recover the target states in a deterministic way.Zha et al[13]investigated the bidirectional controlled quantum teleportation (BCQT) of arbitrary singlequbit states using a five-qubit cluster state as the entangled resource with unit success probability.Because of its potential application in quantum network communication, BCQT has recently acquired a lot of attention.[14–27] Jiang et al [14]developed a deterministic BCQT scheme for single-qubit states utilizing a five-qubit non-maximally entangled channel.[17–19] accomplished the BCQT of two-qubit states via different entangled resources.Apart from the symmetric protocols, [14–19] there are many asymmetric BCQT protocols [20–25].For example, [20–24] describe the BCQT of arbitrary single-and two-qubit states.Thapliya et al[26]gave a general method for selecting a quantum channel for BCQT.To our knowledge, few universal protocols have been described for arbitrary qubit states.Savaghad-Moghaddam et al [27] attempted to investigate the BCQT of m- and n-qubit states.Regretfully, they did not explicitly give the relationship between the recovery operations, the collapsed states, and the measurement results.A question may be naturally raised: is it possible to devise a universal and efficient BCQT protocol for arbitrary qubit states and give a general formula for the recovery operations?
In this paper, under the assumption that classical communication is not allowed between senders and that the controller has a broadcast channel, we propose a universal protocol to realize the two-way teleportation of arbitrary n1-and n2-qubit states with the help of the controller via a(2n1+2n2+1)-qubit maximally entangled state.Without loss of generality, we assume n1≤n2.After the the sender’s projective measurement using the Bell basis and the controller’s single-qubit measurement using the Z basis, the receiver performs single-qubit Pauli operations and gets the target state deterministically.Through rigorous deduction,we give the general expression for the recovery operators.Network coding, a new paradigm that allows information to be duplicated and mixed in the intermediate nodes, has demonstrated a significant throughput advantage over traditional routing algorithms in classical networks [28].It is found that if network coding is applied at the controller’s site, a(2n1+1)-bit classical communication cost (CCC) will be saved in the broadcast channel.This means that our protocol is more efficient than without network coding.
The remaining parts of this paper are arranged as follows.In section 2, an explicit symmetric BCQT protocol is proposed to realize the two-way teleportation of two-qubit states.In section 3, an asymmetric BCQT protocol is described for single- and two-qubit states.In section 4, we further extend our discussion to a universal BCQT protocol for arbitrary n1-and n2-qubit states by using a (2n1+2n2+1)-qubit state as the entangled channel.Some discussions and comparisons are given in section 5.The last section offers the conclusions.
2.The symmetric BCQT protocol for two-qubit states
In this section,we construct a controlled protocol that leads to the simultaneous exchange of arbitrary two-qubit states.There are three participants: Alice, Bob, and Charlie.Alice and Bob are not only senders but also receivers,while Charlie is the controller.
Suppose Alice intends to teleport an arbitrary two-qubit state∣φ〉A1A2to Bob.At the same time,Bob wishes to teleport an unknown two-qubit state∣ψ〉B1B2to Alice’s site.


The quantum channel shared amongst the three participants is the nine-qubit entangled state
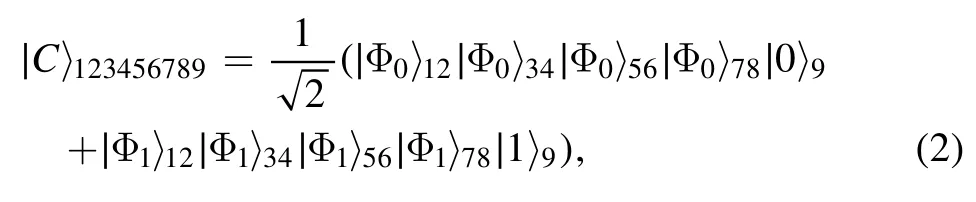
where
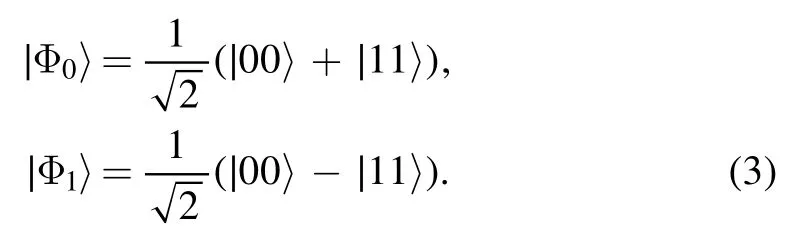
Qubits(1,3,5,7)belong to Alice,qubits(2,4,6,8)belong to Bob, and qubit 9 is held by Charlie.
Hence,the initial state of the whole system can be written as

The complete process of the symmetric protocol is described as follows.
Step 1.Alice (Bob) performs joint projective measurements on her(his)qubits(A1,1)and(A2,3),((B1,6)and(B2,8)) using the Bell basis
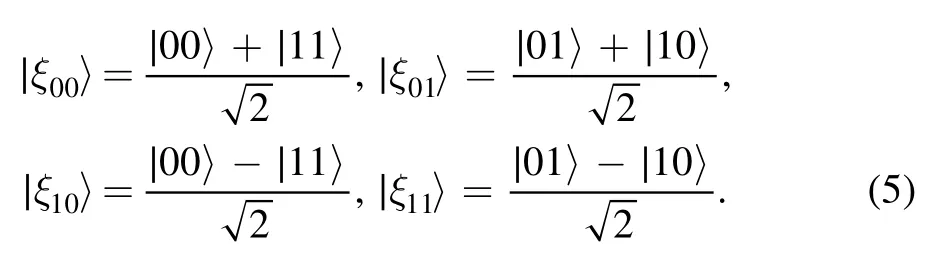
After the measurements, Alice announces her measurement resultsto Charlie in the form of classical messages pjqj.Similarly, Bob sends four-bit classical information sjtjto Charlie corresponding to his measurement outcomesHere, pj, qj, sj, tj=0, 1, j=1, 2.
Based on the measurement bases, the joint system in equation (4) can be expressed as
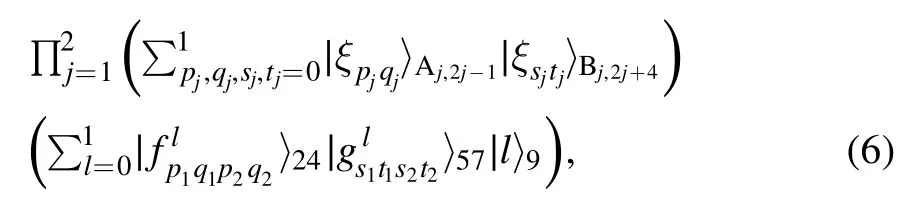
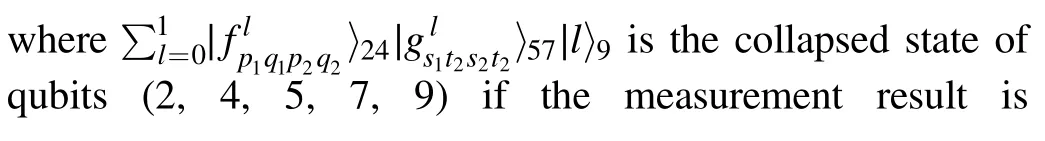
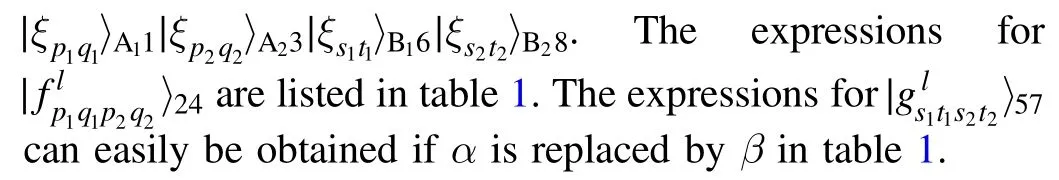
Table 1.The expressions for and the recovery operations (RO).

Table 1.The expressions for and the recovery operations (RO).
p1q1, p2q2 l p1q1, p2q2 l 〉fp q p q l 1 1 2 2∣RO 00,00 0 10,10 1 α0|00〉+α1|01〉+α2|10〉+α3|11〉 I ?I 00,01 0 10,11 1 α0|01〉+α1|00〉+α2|11〉+α3|10〉 I ?X 00,10 0 10,00 1 α0|00〉?α1|01〉+α2|10〉?α3|11〉 I ?Z 00,11 0 10,01 1 α0|01〉?α1|00〉+α2|11〉?α3|10〉 I ?(ZX)01,00 0 11,10 1 α0|10〉+α1|11〉+α2|00〉+α3|01〉 X ?I 01,01 0 11,11 1 α0|11〉+α1|10〉+α2|01〉+α3|00〉 X ?X 01,10 0 11,00 1 α0|10〉?α1|11〉+α2|00〉?α3|01〉 X ?Z 01,11 0 11,01 1 α0|11〉?α1|10〉+α2|01〉?α3|00〉 X ?(ZX)10,00 0 00,10 1 α0|00〉+α1|01〉?α2|10〉?α3|11〉 Z ?I 10,01 0 00,11 1 α0|01〉+α1|00〉?α2|11〉?α3|10〉 Z ?X 10,10 0 00,00 1 α0|00〉?α1|01〉?α2|10〉+α3|11〉 Z ?Z 10,11 0 00,01 1 α0|01〉?α1|00〉?α2|11〉+α3|10〉 Z ?(ZX)11,00 0 01,10 1 α0|10〉+α1|11〉?α2|00〉?α3|01〉 (ZX)?I 11,01 0 01,11 1 α0|11〉+α1|10〉?α2|01〉?α3|00〉 (ZX)?X 11,10 0 01,00 1 α0|10〉?α1|11〉?α2|00〉+α3|01〉 (ZX)?Z 11,11 0 01,01 1 α0|11〉?α1|10〉?α2|01〉+α3|00〉 (ZX)?(ZX)
At this moment,Alice and Bob cannot obtain the original states without the controller’s (Charlie’s) help.
Step 2.If Charlie would like to provide assistance, he makes a single-qubit measurement of his qubit 9 using the Z basis {|0〉, |1〉} and broadcasts a classical message to Alice and Bob.
It seems that Alice and Bob need to obtain the measurement results s1t1s2t2l and p1q1p2q2l to recover the teleported states, respectively.This means that Charlie has to broadcast nine-bit classical messages.Using the technology of network coding, Charlie just broadcasts the four-bit classical information(pj⊕sj⊕l,qj⊕tj)to Alice and Bob(j=1,2).Here ⊕means plus mod 2.
Step 3.According to the received classical messages and her (his) own measurement results pjqj(sjtj), Alice calculates[pj⊕(pj⊕sj⊕l), qj⊕(qj⊕tj)] and gets [sj⊕l, tj].Bob computes [sj⊕(pj⊕sj⊕l), tj⊕(qj⊕tj)] and obtains [pj⊕l,qj].Then Alice performs the recovery operation,
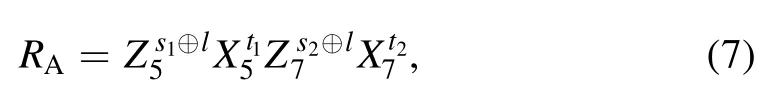
on her qubits (5, 7) and gets |ψ〉.Similarly, Bob carries out the appropriate operation,
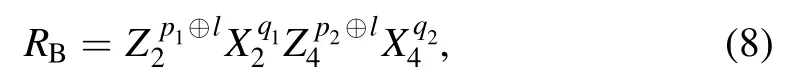
on his qubits(2,4)and recovers the two-qubit state|φ〉.Here X, Z are Pauli operations and X0, Z0denote identity operations.In detail, Alice’s and Bob’s recovery operations conditioned on the measurement results are listed in table 1.
To illustrate the protocol more clearly, we assume that Alice’s measurement results are |ξ01〉|ξ10〉 (p1q1=01,p2q2=10) and Bob’s measurement results are |ξ00〉|ξ11〉(s1t1=00, s2t2=11).If Charlie’s measurement result is |1〉,then the qubits (5, 7, 2, 4) collapse into:
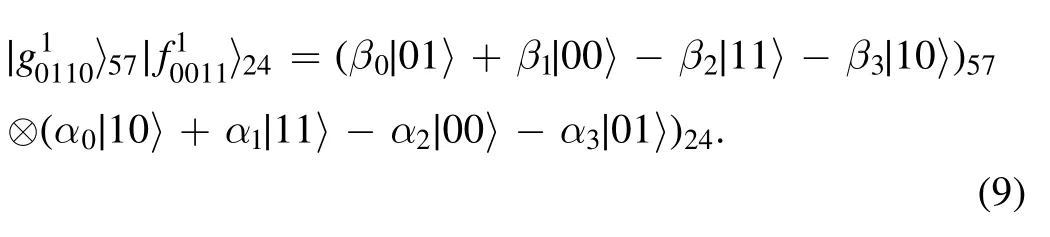
Charlie broadcasts the four-bit classical information(p1⊕s1⊕l, p2⊕s2⊕l, q1⊕t1, q2⊕t2)=1111.Together with their own measurement results,Alice and Bob can obtain(s1⊕l, s2⊕l, t1, t2)=1001 and (p1⊕l, p2⊕l, q1,q2)=1010, respectively.Alice performs a Z5X7operation on her collapsed qubits(β0∣0 1〉 +β1∣0 0〉 -β2∣1 1〉 -β3∣ 1 0〉)57and Bob carries out (ZX)2I4on his collapsed qubits(α0∣1 0〉 +α1∣1 1〉 -α2∣0 0〉 -α3∣ 0 1〉)24.As a result, the desired states |φ〉, |ψ〉 are simultaneously teleported.
3.The asymmetric BCQT protocol for single- and two-qubit states
In this section, we demonstrate an asymmetric BCQT protocol.Alice wants to teleport an arbitrary single-qubit state|φ〉Ato Bob, while Bob hopes to transmit an arbitrary two-qubit state∣ψ〉B1B2to Alice.
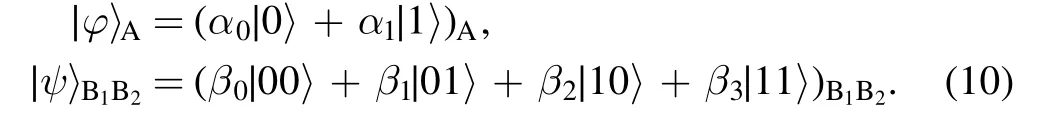
The coefficients of the teleported states are all complex numbers, and satisfy the normalization condition=1.
A seven-qubit entangled state,
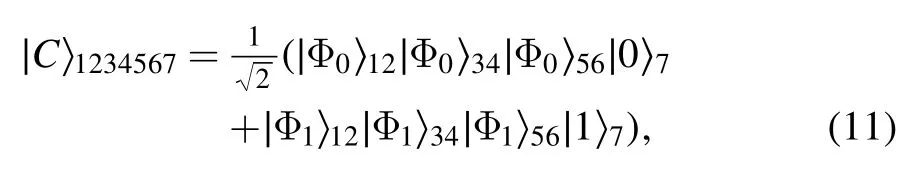
serves as the quantum channel.Alice has qubits(1,3,5)and Bob processes qubits(2, 4,6),while qubit 7 is possessed by Charlie.
Table 2.Expressions forand the RO.
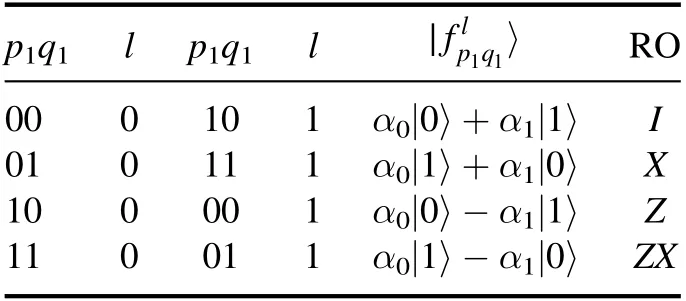
Table 2.Expressions forand the RO.
p1q1 l p1q1 l f 〉p q l 1 1∣RO 00 0 10 1 α0|0〉+α1|1〉 I 01 0 11 1 α0|1〉+α1|0〉 X 10 0 00 1 α0|0〉?α1|1〉 Z 11 0 01 1 α0|1〉?α1|0〉 ZX
The compound state is
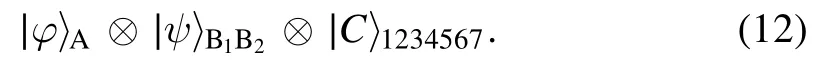
The detailed process of the asymmetric protocol is shown below.
Step 1.Alice (Bob) carries out a Bell basis measurement on her (his) qubits (A, 1) ((B1, 4) and (B2, 6)).If Alice’s (Bob’s)measurement result isshe(he)sends the classical bits p1q1(sjtj) to Charlie through the classical channel.
The whole system in equation (12) can be rewritten as
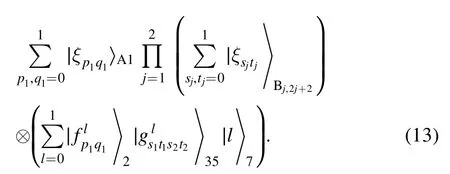

Step 2.Charlie measures his qubit 7 in the Z basis.In order to recover the teleported state, Alice and Bob need to obtain the measurement results s1t1s2t2l and p1q1l, respectively.With the aid of network coding,Charlie broadcasts the four-bit classical information (s1⊕p1⊕l, t1⊕q1, s2⊕l, t2).
Step 3.According to the received classical messages and her (his) own measurement result p1q1(s1t1, s2t2), Alice gets[s1⊕l, t1, s2⊕l, t2] by calculating [p1⊕(s1⊕p1⊕l),q1⊕(t1⊕q1)].Similarly, Bob computes [s1⊕(s1⊕p1⊕l),t1⊕(t1⊕q1)] and acquires [p1⊕l, q1].Alice applies the recovery operation,
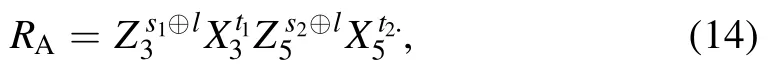
on her qubits (3, 5) and gets |ψ〉 in equation (10).Bob can recover the teleported state |φ〉 by performing the unitary operation,

on his collapsed particle 2.
An example is given below to clarify the protocol.Suppose that Alice’s measurement outcome is |ξ01〉(p1q1=01) and Bob’s measurement outcomes are |ξ01〉|ξ10〉(s1t1=01, s2t2=10).If Charlie’s measurement result is |0〉,he broadcasts the four-bit classical information (s1⊕p1⊕l,t1⊕q1,s2⊕l,t2)=0010.Alice and Bob can then get(s1⊕l,t1,s2⊕l,t2)=0110 and(p1⊕l,q1)=01,respectively.Alice and Bob separately perform the recovery operations X3Z5and X2on the collapsed state:
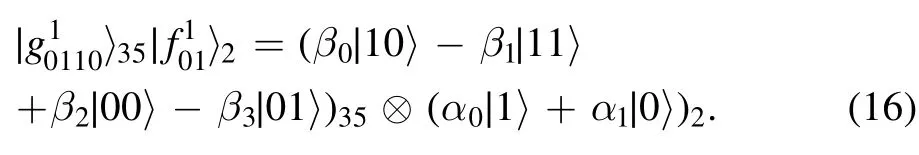
In the end,the desired states are two-way teleported with unit success probability.
4.The universal BCQT protocol
In this section,we generalize the two explicit protocols given above to a universal BCQT protocol that can realize the simultaneous teleportation of arbitrary n1-and n2-qubit states.
Alice(Bob)has an unknown n1(n2)-qubit state in this form:
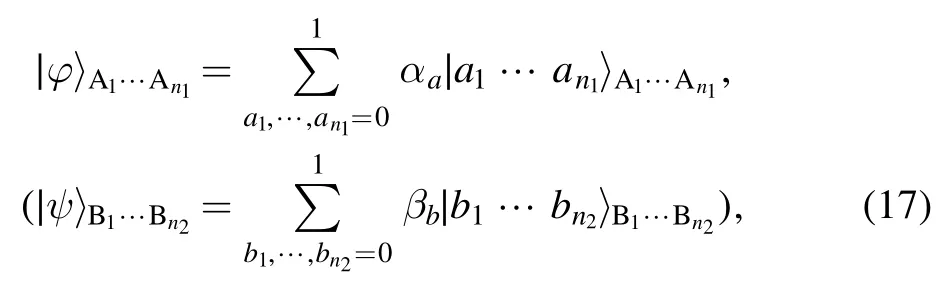
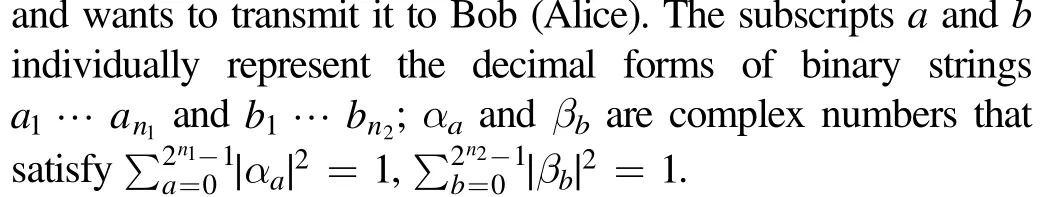
We take a (2n1+2n2+1)-qubit entangled state,
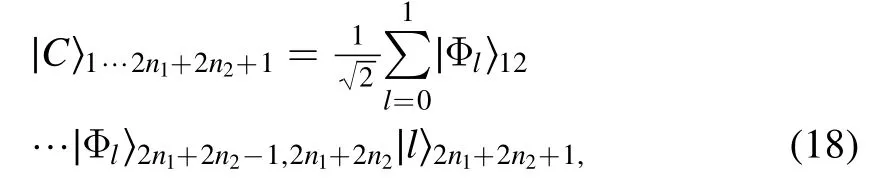
as the quantum channel.The construction process of the channel is similar to that given in [29].The qubits(1, …,2n1?1, 2n1+1, …,2n1+2n2?1) belong to Alice,the qubits (2, …,2n1, 2n1+2, …,2n1+2n2) belong to Bob,and the controller Charlie possesses the qubit 2n1+2n2+1.
The initial state of the whole system is given by
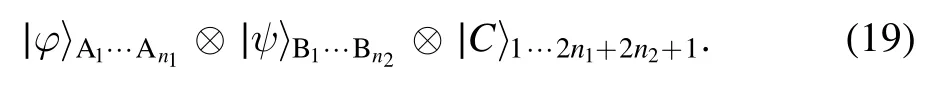
In order to complete the task, the three participants are required to perform appropriate measurements and corresponding recovery operations.The process of our universal BCQT protocol is shown in figure 1.
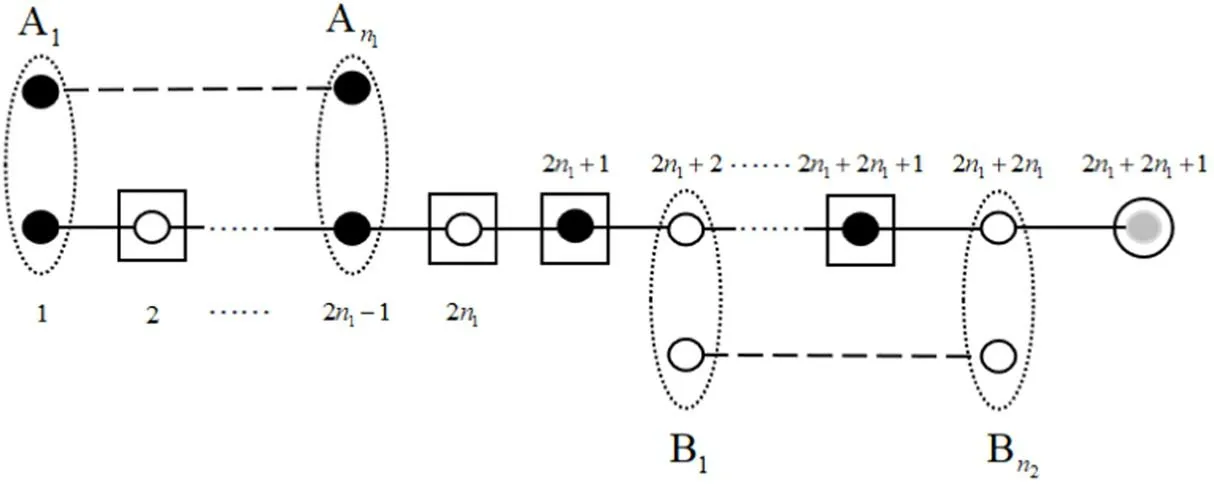
Figure 1.Process of our universal BCQT protocol.Black solid points represent Alice’s particles,white points represent Bob’s particles,and the gray point represents Charlie’s particle.The dotted ellipses indicate Bell-state measurements, and the solid circle is a single-qubit measurement.The solid rectangle indicates the recovery operation.
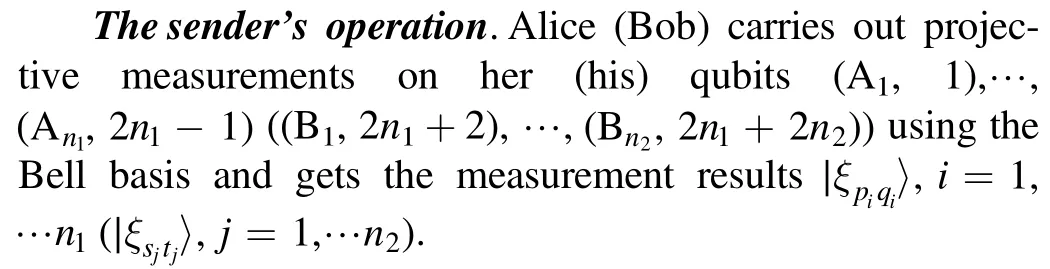
Then, Alice (Bob) sends the classical bits piqi(sjtj) to Charlie, representing the Bell-state measurement outcomes.
The compound system in equation(19)can be rewritten as
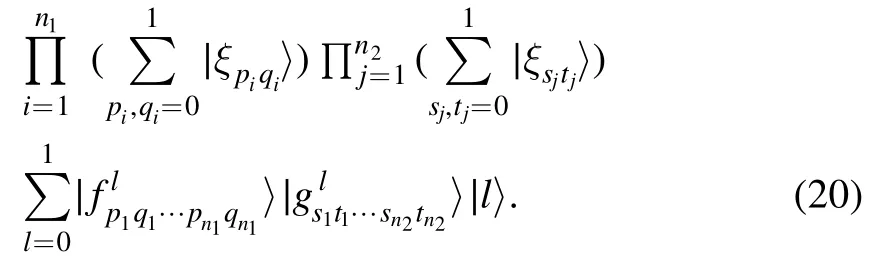

Since
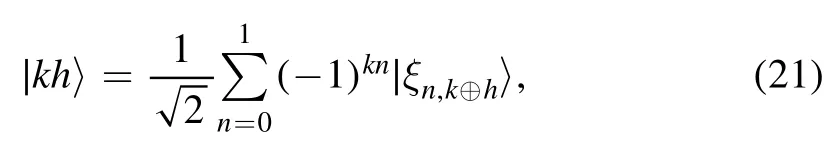
one can get
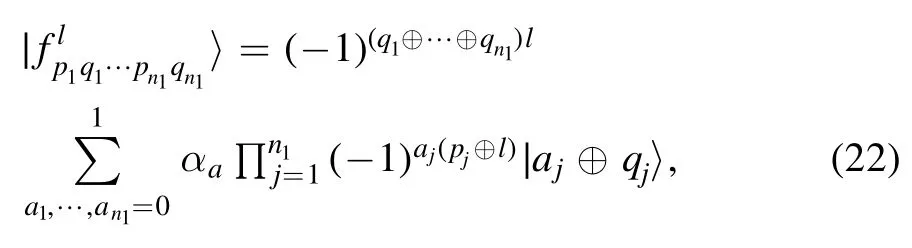
and
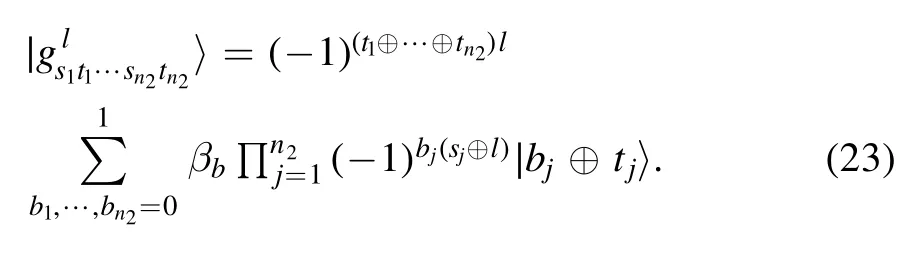
At this time, Alice and Bob are still unable to complete the task without Charlie’s assistance, since their qubits are entangled with Charlie’s qubit 2n1+2n2+1.
The controller’s operation.If Charlie consents to help them, he executes a single-qubit projective measurement using the Z basis.
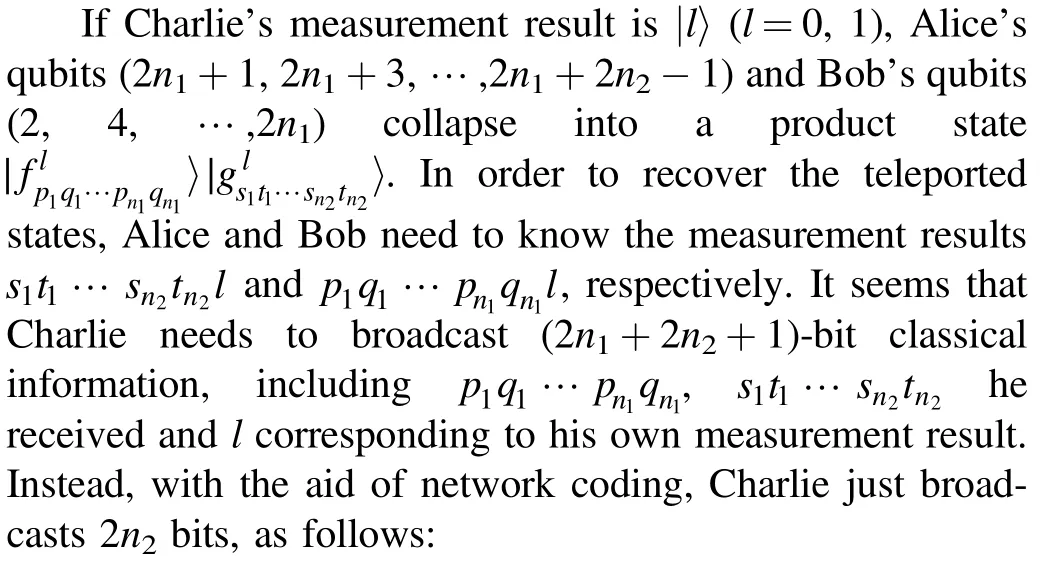
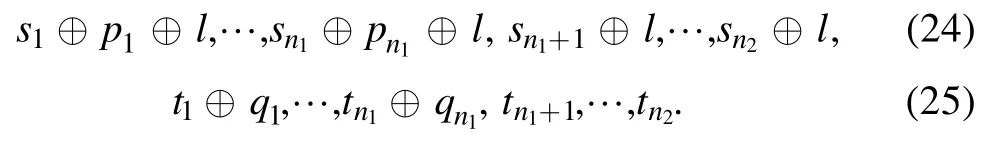
This means that a (2n1+1)-bit CCC is saved.
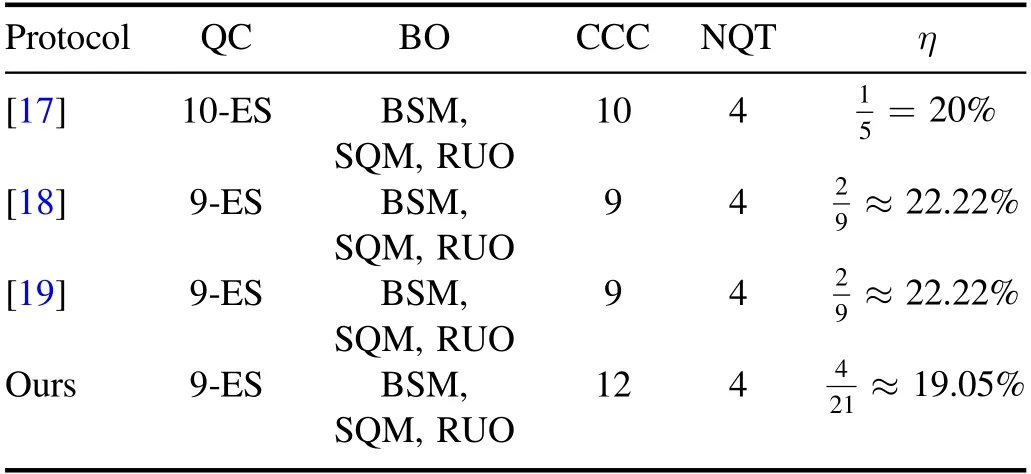
Table 3.Comparison of the symmetric protocol for two-qubit states(n1=n2=2).
The receiver’s operation.According to the classical messages received from Charlie and her (his) own measurement results, Alice calculates

Together withsn1+1⊕l, … ,sn2⊕l,tn1+1,…,tn2, Alice gets[sj⊕l, tj], j=1,..., n2.Bob computes

and gains [pi⊕l, qi], i=1…n1.Using equations (22) and(23), Alice and Bob perform the recovery operations RAand RBon their qubits, which can be summarized as
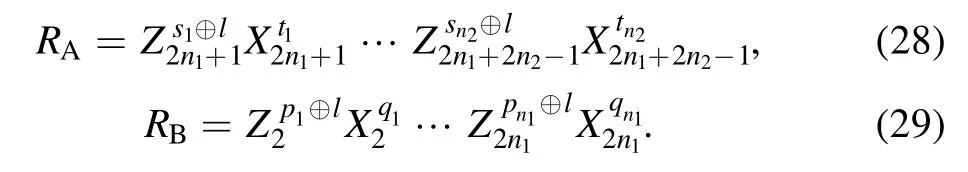
Accordingly, the BCQT is achieved with a success probability of 100%.
5.Discussion and comparisons
In this section, we first discuss the intrinsic efficiency [18]and the necessary operations of our universal protocol.Then,some comparisons with other protocols are given.
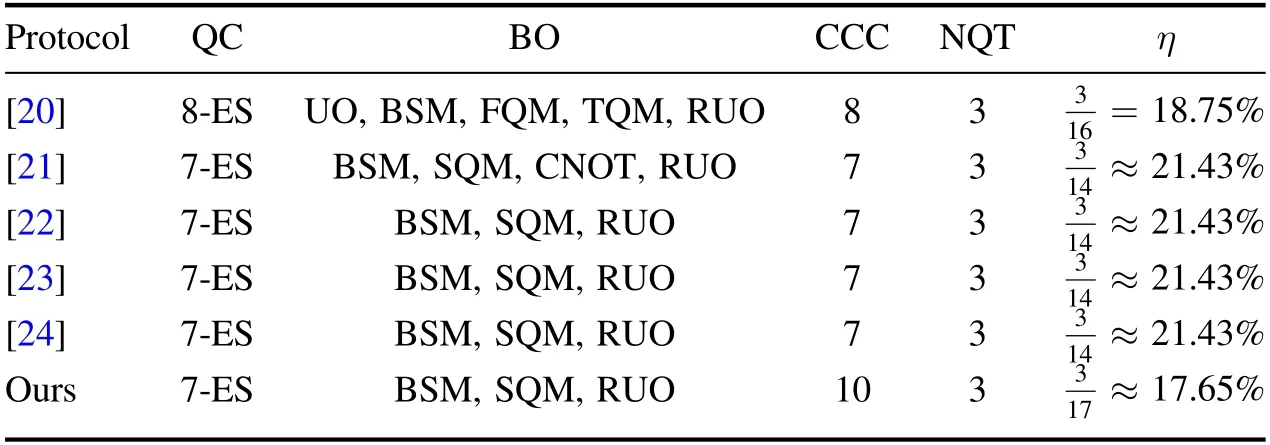
Table 4.Comparison of the asymmetric BCQT protocol for single- and two-qubit states (n1=1, n2=2).
The intrinsic efficiency is an important factor for evaluating the performance of a protocol, which is defined by

where qsrepresents the number of qubits to be transmitted,quis the number of particles used in the quantum channel,and btrepresents the classical bits that need to be transmitted.
As mentioned above, we propose a universal BCQT protocol for arbitrary n1-and n2-qubit states,which can be realized deterministically.The (2n1+2n2+1)-qubit entangled state is chosen as the quantum channel.Alice and Bob respectively transmit 2n1and 2n2bits to the controller Charlie.Charlie encodes his classical information corresponding to his measurement result with the classical messages he received,and then broadcasts the encoded result to Alice and Bob.The CCC in the controller’s broadcast channel is 2n2bits.The total CCC is 2n1+4n2bits.Therefore,the intrinsic efficiency of our universal protocol is
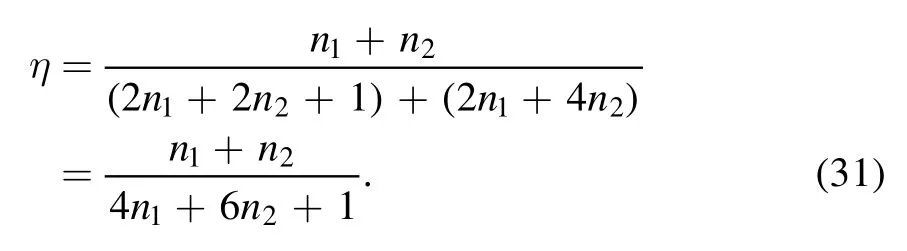
In our symmetric BCQT protocol for arbitrary two-qubit states(n1=n2=2), the intrinsic effciiency is≈19.05%.In our asymmetric BCQT protocol for arbitrary single- and twoqubit states (n1=1, n2=2), the intrinsic efficiency is≈17.65%.
If network coding is not applied, the total CCC is 4n1+4n2+1 bits.The intrinsic efficiency of the universal protocol will be
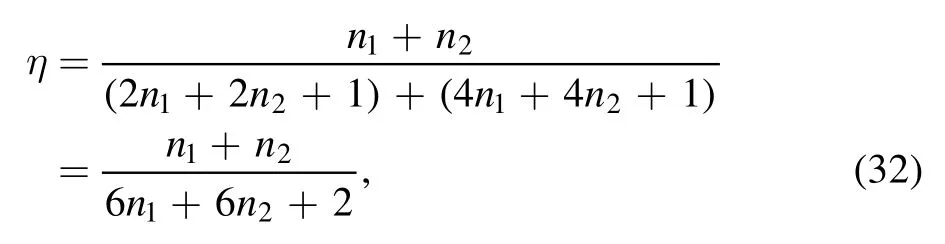
which is smaller than the intrinsic efficiency in equation(31).In this case, the intrinsic efficiency of the symmetric BCQT protocol is≈15.39%.When n1=1 and n2=2, the intrinsic efficiency is≈15%.This reveals that the use of network coding technology can reduce the CCC and improve the intrinsic efficiency.
In the following, we give some comparisons with other BCQT protocols.To make the comparison convictive, we only choose some specific values of n1, n2.The results of comparisons with previous symmetric and asymmetric protocols are given in tables 3 and 4, respectively.A detailed explanation of the abbreviations is as follows: QC (quantum channel), ES (entangled state), BO (basic operation), UO(unitary operation), RUO (recovery unitary operation), BSM(Bell-state measurement), SQM (single-qubit measurement),TQM (two-qubit measurement), FQM (four-qubit measurement), CNOT (controlled-NOT), NQT (number of the teleported qubits).
From tables 3 and 4, one can see that the intrinsic efficiencies of [17–24] are all greater than ours.The reason for this is that the classical channel model they use is different from ours.Classical channel models are clearly shown in figure 2, where (a) represents the model of [17–24], and (b)represents our model.As well as the unfavorable aspects,our scheme also has favorable aspects.The classical channel models in [17–24] assume that each sender broadcasts her measurement result.In other words,everyone has a broadcast channel.This may reduce the CCC and improve the intrinsic efficiency;however,the establishment of a broadcast channel is much more difficult than that of a one-way classical channel.For an actual communication network with multiple users and a control center, it is not realistic to set up a broadcast channel for each user.In our model, each sender only has one classical channel with the controller, which greatly reduces the requirement for classical channels.Moreover,our model may be more applicable and safer in the case that direct classical communication is not allowed between different users,and the role of the controller is to be a transmission relay or trusted third party.
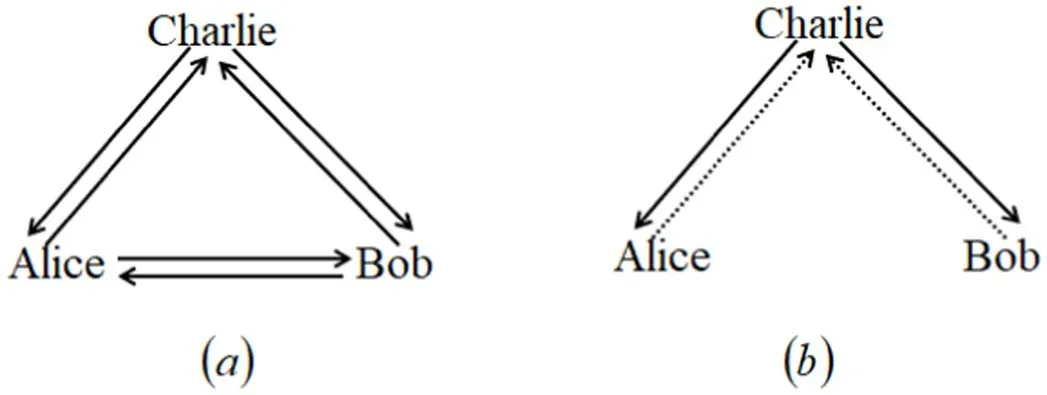
Figure 2.Classical channel models.(a) The usual model; (b)our model.A solid line with one arrow denotes a one-way broadcast channel,while a dotted line with one arrow denotes a one-way classical channel.
6.Conclusions
Assuming that the two senders cannot transmit classical messages to each other and that the controller has a broadcast channel, we have devised a universal protocol for the twoway teleportation of arbitrary n1- and n2-qubit states.The proposed scheme has the following advantages.(i) Through strict derivation, the recovery operator is given by a general formula which clearly reveals the relationship with the measurement results.(ii) Network coding is performed at the site of the controller.It is easy to see if the network coding is not applied; a (2n1+2n2+1)-bit CCC is required for Charlie’s broadcast channel.Therefore,a(2n1+1)-bit CCC is saved.It may be helpful to realize secure quantum distributed transmission tasks with a reduced CCC.We also believe that network coding may be useful for saving resources in various quantum network information-processing tasks.
The construction of the quantum channel only needs H and CNOT gate operations on the auxiliary particles with an initial state of ∣0 0 … 0〉1…2n1+2n2+1.The process of the universal protocol requires Bell-basis measurement, Z-basis measurement, and single-qubit local Pauli operations.These are feasible with the current experimental technology.It should be noted that quantum entanglement is indispensable in most existing BCQT schemes.However, from a practical point of view, entanglements are often very vulnerable and may suffer from destructive influences, or even disappear completely.Therefore, the effects of noise should be taken into account.Similarly to [8, 9], we can envisage the proposed scheme in a noisy environment.Fortunately, some mature anti-noise techniques, such as entanglement purification and entanglement concentration, can be employed to improve the fidelity of the transmitted quantum signals and reduce the effects of noise.
Acknowledgments
This work is supported by the National Natural Science Foundation of China (Grant Nos.61 201 253, 61 572 246),the Open Foundation of State Key Laboratory of Networking and Switching Technology (Beijing University of Posts and Telecommunications) (Grant No.SKLNST-2020-2-02), and the Open Foundation of Guangxi Key Laboratory of Trusted Software (Grant No.KX202040).
 Communications in Theoretical Physics2021年10期
Communications in Theoretical Physics2021年10期
- Communications in Theoretical Physics的其它文章
- Analysis of the wave functions for accelerating Kerr-Newman metric
- Three-dimensional massive Kiselev AdS black hole and its thermodynamics
- Examination of n-T9 conditions required by N=50, 82, 126 waiting points in r-process
- Scalar one-loop four-point integral with one massless vertex in loop regularization
- Strange quark star and the parameter space of the quasi-particle model
- Improved analysis of the rare decay processes of Λb
